Introduction
The next generation of wireless and mobile network, called 5G1, is expected to become the most important network of the 21st century and is predicted to have a decade-long impact. 5G’s deployment started in 2019, and since then a ‘race’ has been ongoing between governments, industries, and investors to be the first to build a functional network. 2020 is expected to be the year that 5G will be globally launched and by 2025, 15% of global mobile connections will be based on it2. The worldwide 5G revenues in 2025 are anticipated to reach € 225 billion3.
5G is gradually replacing the 4G/LTE4 network which was released in March 20095 and introduced ground-breaking, for that period, fast connection speeds and mobile hotspots. 5G technology, based on the 802.11ac IEEE wireless standard6, is expected to boost data transmission and communication by over three times while simultaneously guaranteeing ultra-high reliable and resilient connections. In the 3G and 4G world, speed and throughput were the most important characteristics to differentiate a network. The amount of data that a network could relay and the upload and download speed were the main features for users or services. But in a future 5G world this is not enough; 5G technology is not simply a faster version of 4G, but rather, an entirely new network architecture7.
Technical Characteristics
The three main technical characteristics of 5G networks are:
- Data rates of between 1–20 Gbit/s per mobile base station, at least 10 times faster than before, allowing users on the same cell to quickly download a large volume of data.
- Latency speed less than 1ms, virtually eliminating any delays or lags when requesting data from the network.
- Increased capacity to connect not only a high number of individual users but also more objects per specific geographical area.
The three characteristics above, together with mobility (staying connected while travelling at high speeds), energy efficiency (switching inactive radio interfaces into low-energy mode), service deployment and reliability, synthesize the key features of 5G networks that make them unique and, indeed, revolutionary as they promise to expand our ways of communication and completely transform our way of living.
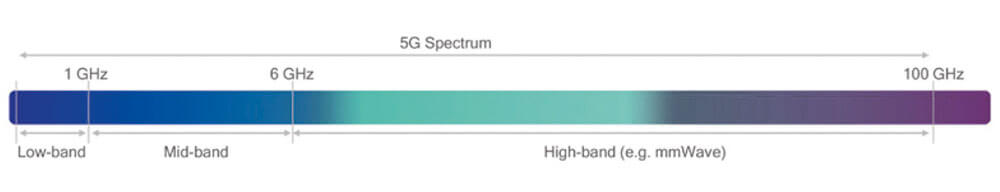
5G’s network infrastructure will no longer be based on the combination of specialised hardware and software elements. Instead, customization and functionality will take place only in the software. A new core network will support ‘network slicing’ features which will provide different service layers on the same physical network8. 5G, unlike previous technology, operates on three different spectrum bands (high, medium and low – see figure on next page) with each band having specific characteristics suitable for certain deployment scenarios. Finally, a more decentralized architecture than the traditional one in 4G will allow the network to steer traffic at the ‘edge of the network’ while still ensuring low response times.
5G technology enhanced by Artificial Intelligence (AI) is accelerating the development and implementation of technologies such as Connected Autonomous Vehicles (CAVs), ‘smart cities’, Virtual Reality (VR) and Augmented Reality (AR). Moreover, 5G networks contribute to a huge rise in the number of components in the Internet of Things (IoT), massively increasing the number and diversity of interconnected devices. It is predicted that around 75,44 billion devices worldwide will be ‘online’ by 20259, virtually connecting ‘everything to everything’ (X2X). Subsequently, 5G has the potential to transform the employment of military air operations and enhance its capabilities with components and functions that never existed before.
Cyber Threats
However, from a cyber-space perspective, 5G technology also increases drastically the attack surface (in some ways previously non-existent) and the number of potential entry points for attackers. The increased speed of the connected devices could make them more vulnerable to Distributed Denial-of-Service (DDoS) attacks. In today’s era of 4G/LTE mobile Internet, a large botnet10 formed simply by hacking a user’s home devices could be used to launch large-scale DDoS attacks against websites; in tomorrow’s 5G network era, a similar botnet could disrupt an entire network of autonomous cars in a city11. As a result, the wide range of services and applications, as well as the novel features in the architecture, will introduce a plethora of new security challenges.
It was in September 2016 when hackers succeeded in scanning and exploiting hundreds of thousands of low-cost and low-powered IoT devices such as IP cameras, home routers, and digital video recorders, and turned them into remotely controlled bots by using ‘Mirai’ malware to launch large scale DDoS attacks. Not only 5G technology itself but also the communication between devices connected to the internet can be the weakest link in 5G’s security. If the manufactures of those low-cost interconnected devices do not embed cybersecurity standards in their products, the security risks will remain high.
5G networks and smart devices must adopt reliable and long-term security requirements beginning in the early stages of the design and manufacturing processes in order to fulfil their technological promises. By embracing a structured ‘cyber hygiene policy’, 5G technology can eventually be effectively implemented in Air Operations to improve communications and situational awareness.
Enhancing Air Power
NATO Allied Forces can gain great advantages by leveraging the novel features of 5G cellular technology. Communications and network operations in the air battlespace will be able to handle far more data at much faster speeds supporting real-time video streaming and VR applications. The wide employment of Unmanned Aerial Vehicles (UAVs) for purposes ranging from Intelligence, Surveillance & Reconnaissance (ISR) to airstrikes is expected to evolve even further in terms of geographic coverage and efficiency. Even logistic and maintenance activities, such as tracking maintenance stocks and conducting technical inspections, could benefit from a reliable and secure mobile connectivity.
Modern logistics systems such as the Autonomic Logistics Information System (ALIS) for the Joint Strike Fighter, are integrated with maintenance and operations procedures from across the world identifying problems with the aircraft, installing software updates, and providing preventive actions. 5G technology can clearly enhance productivity and safety of such complex, large-scale and interconnected military logistics operations transforming them to ‘sophisticated weapon systems’ ready to use even on the battlefield.
5G networks have the ability to expand the range of cloud-based applications and exponentially increase the amount of data transmitted and exchanged during air combat operations. The challenge of infobesity (information overload) can still be encountered using digital technologies that take advantage of the super-fast, high-bandwidth and low-latency communication environment that 5G provides. Consolidating the extracted information from internet-connected sensors and platforms, and immediately distributing the acquired knowledge to the Command and Control structure is essential to facilitate ‘smart’ decision-making12. Therefore, securing (allied) military networks and maintaining their high level of interoperability will become even more critical.
According to an ‘EU coordinated risk assessment report’13, published on 9 October 2019, among the main threats and vulnerabilities of 5G networks are the high dependencies on individual suppliers. The lack of diversity in equipment and infrastructure can lead to increased exposure to attacks by State-sponsored actors who interfere with the suppliers. Thus, the individual risk profile of suppliers will become particularly important, especially for those with significant presence within networks.
In order to develop a secure 5G mobile network strategy, the US Department of Defence (DoD) decided, about a year ago, to strengthen the requirements for the supply chain of innovative technology products, including subcontractors, by introducing higher cybersecurity standards that would ensure resiliency to cyber-attacks. The established public-private partnership, known as ‘Trusted Capital Marketplace’, connects defence technology start-ups with trusted sources of capital in order to secure the delivery of such critical emerging technologies14.
Future Challenges
With the future stand-alone 5G ecosystem, as described above, all network functionalities will be virtualised based on software rather than hardware, and take place within a single cloud environment. 5G networks are going to be deployed in a complex global cybersecurity threat landscape. To ensure confidentiality (authorised access), integrity (accurate information) and availability (any time access) with such a revolutionary technology and confront the challenges derived from it, NATO member and partner countries will have to follow a new security paradigm. Current cybersecurity models and policies must be reassessed and new security frameworks applied in order to mitigate risks and threats.
Are Alliance members determined to invest the resources necessary for establishing a resilient and secure infrastructure for 5G technology? Are we willing to adapt to this emerging technology at the speed of change and not lagging behind other competing nations? Those questions have to be answered as clearly and decisively as possible in the very near future.