Introduction
Targeting is the means of selecting targets to meet a commander’s intent and prioritizing them systematically so that the most important are prosecuted first. It includes both a lethal and non-lethal approach by which to prosecute targets and is dependent on the campaign and the intent of the commander. Targets will differ in each campaign.
There are many different ways to organize a nation’s or an alliance’s targeting approach. The US Joint Publication 3-60 (Joint Targeting), for example, outlines a targeting cycle that supports the Joint Force Commander’s (JFC’s) joint operational planning and execution with a comprehensive, iterative, and logical methodology for employing the ways and means to create desired effects that support the achievement of objectives.1 A representation of this targeting cycle is outlined in Figure 9.1 below.
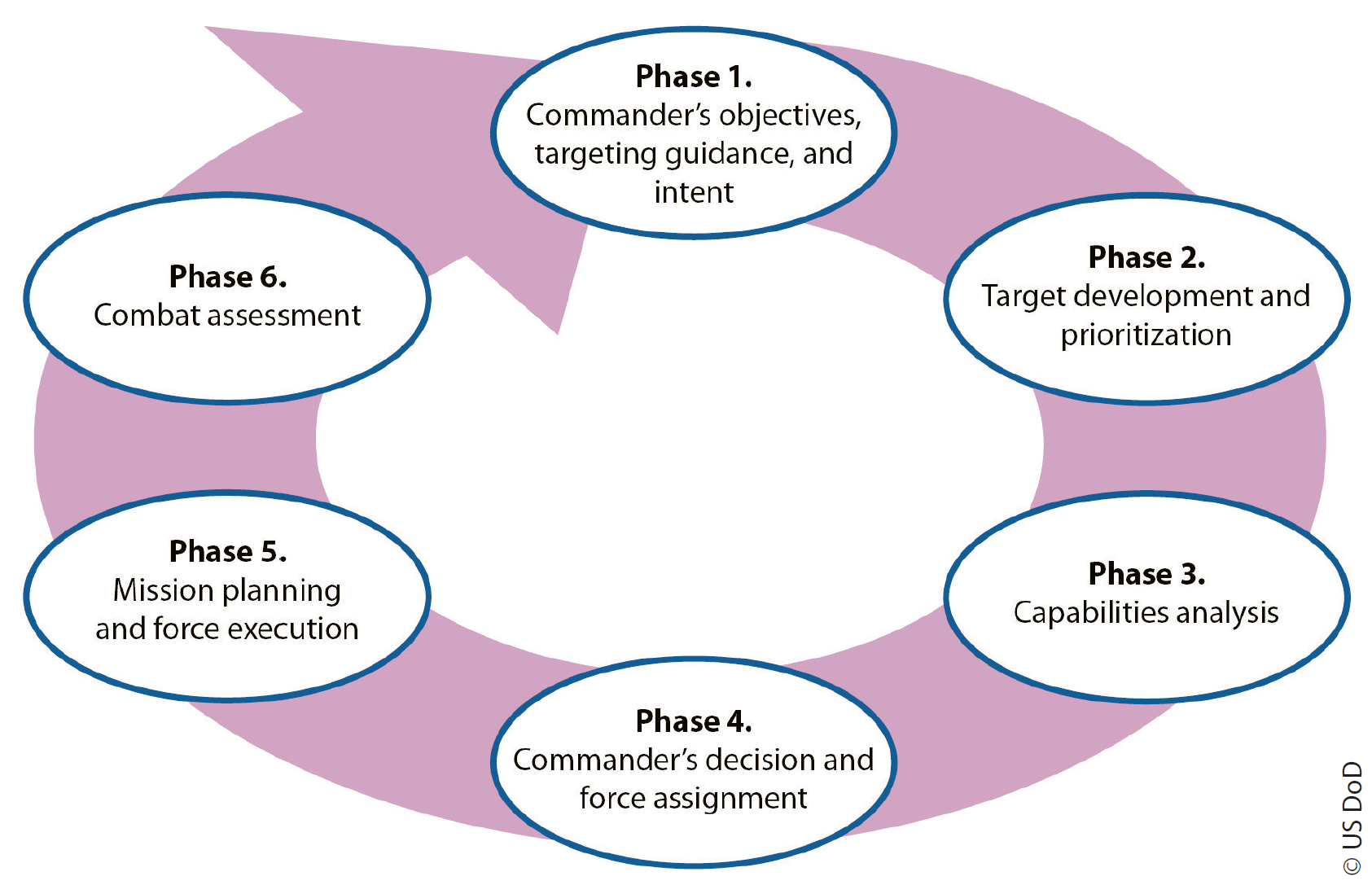
NATO follows a similar methodology, which is based on an approach that prioritizes targets based on strategic and operational value. It is unlikely that Unmanned Aircraft Systems (UAS) would feature highly in the prioritized list of targets where issues of contested airspace, freedom of manoeuvre or denied areas are prevalent. Both large and small drones would not be appropriately targeted from a strategic or operational point of view, similar to individual tanks or aircraft, but their systems and the overall effect they may be having could be targeted, again, depending on the campaign and its objectives.
It should also be noted that targeting and defending are two different categories which do not systematically meet. One is focused on enemy forces and their destruction whereas the other concentrates on friendly forces’ assets and their protection (i.e. a Defended Asset List (DAL)). By knowing how to defend against or conduct Counter-Unmanned Aircraft System (C-UAS) operations, one could argue that those systems can be analyzed to target an enemy’s UAS inventory. The offensive targeting of those assets, once the campaign has reached an appropriate point in the conflict to do so, is the focus of this document.
Application of UAS
One of the earliest uses of drones in combat was during the Yom Kippur War of 1973, when Israel launched drones that had traditionally been used as airborne targets, to trigger the Egyptian forces into launching their entire arsenal of anti-aircraft missiles. The Egyptian defences were degraded as a result.2 One could argue that this success is seen as the genesis point for Unmanned Aerial Vehicles (UAV) and UAS in what is now a common feature in most modern militaries.
There are many military applications for drones, and they were primarily exploited for further development after seeing their military advantage during the 1973 conflict. In more modern times, UAS have become more common, and their civilian application from emergency service surveillance to photography and recreation, and even online shopping delivery have been tested and practised. The commonality of drones in society today allows very easy access to something that can be weaponized by those who would use them for terror purposes. There have been several examples of non-formed (non-military) units using them to disrupt modern society. Drones used in terror activities do not need to be packed with explosives to have a significant effect. Examples vary from airport disruption resulting in monetary loss3 to psychological threats to society’s well-being. Although no major attack has been carried out, the threat remains and therefore has a non-lethal effect on a target/population/society, forcing them to take preventive action and, depending on the effect you wish to achieve, having just as effective an outcome.
With NATO’s current focus on ‘near-peer’ studies, as stated by the Supreme Allied Commander Europe (SACEUR) in a recent US Department of Defense Article,4 then it would be reasonable to primarily focus on freedom of manoeuvre and countering Anti-Access Area Denial (A2AD) and applying offensive-drone employment against that type of threat where practicable.
The layered defences that near-peer adversaries have developed through technological advances and networked, integrated systems are the new advancement in area denial which has successfully countered the conventional metal-on-metal fight that would be expected if it came to a conflict. It is unlikely that a modern military force would seek to employ a non-traditional drone attack on major systems as described, let alone utilize a vulnerable offensive military UAS.
The more informed reader would also note that the targeting of systems associated with A2AD, in a contested environment, would need to include everything from personnel, finance, logistics, cyber as well as Command and Control (C2) nodes (a Multi-Domain Operations (MDO) approach), as a head-on attack would yield little success.
It would be reasonable to ‘pigeon-hole’ C-UAS or offensive UAS as a prioritized system for targeting when conditions are set to do so in the battlespace, and not in the early stages of a conflict under the threat of air defence systems. Whilst this is an important area to manage within a conflict, those strategic targets such as A2AD, Inter Continental Ballistic Missiles (ICBM) Threat, etc. would clearly have a commander’s attention at the outset of hostilities as opposed to countering the drone threat. That argument notwithstanding, this is a forum for ‘outside-of-the-box thinking’. What if proxy or Special Forces had small UAS in their arsenal and remotely attacked a sensitive part of an A2AD structure to disable it enough for a conventional attack to be successful? It would require modern western forces to change a dated mindset and accept that the development of these systems outside the norms of modern conflict, and an ever-changing battlespace is an investment well spent.
Unmanned Aircraft System Types
Types of UAS could be viewed in two categories: those which are part of a formed-military unit and reflect the capabilities one would see in a modern, western military force, or those which are off-the-shelf, modified, and utilized for quick, hybrid-type and unattributable attacks by personnel whose actions would be more related to terrorist, militia or even organized crime groups.
From a targeting standpoint, the breaking down of systems that contribute to the output of the UAS, a Target Systems Analysis (TSA), would highlight those contributing systems and their vulnerabilities which, in turn, could then be exploited by a prioritisation of targets through the targeting process.
The targeting process mentioned above would identify fixed infrastructure that houses or supports the operations of larger UAS (e.g. hangars, data links, communications nodes, etc.), whereas the process for dealing with smaller UAS would be more reactive and rely on indications and warnings (intel) and would be dynamically driven as their location and appearance could not be positively identified at the beginning of the targeting cycle. It could be argued that through intelligence-led targeting of these systems and the tracking of personnel integral to the operation of these UAS, one could derive the most effective means of offensively targeting this type of UAS, tracking their whereabouts, identifying their workshops/home base or identifying Tactics, Techniques and Procedures (TTPs).
Target Systems Analysis – General
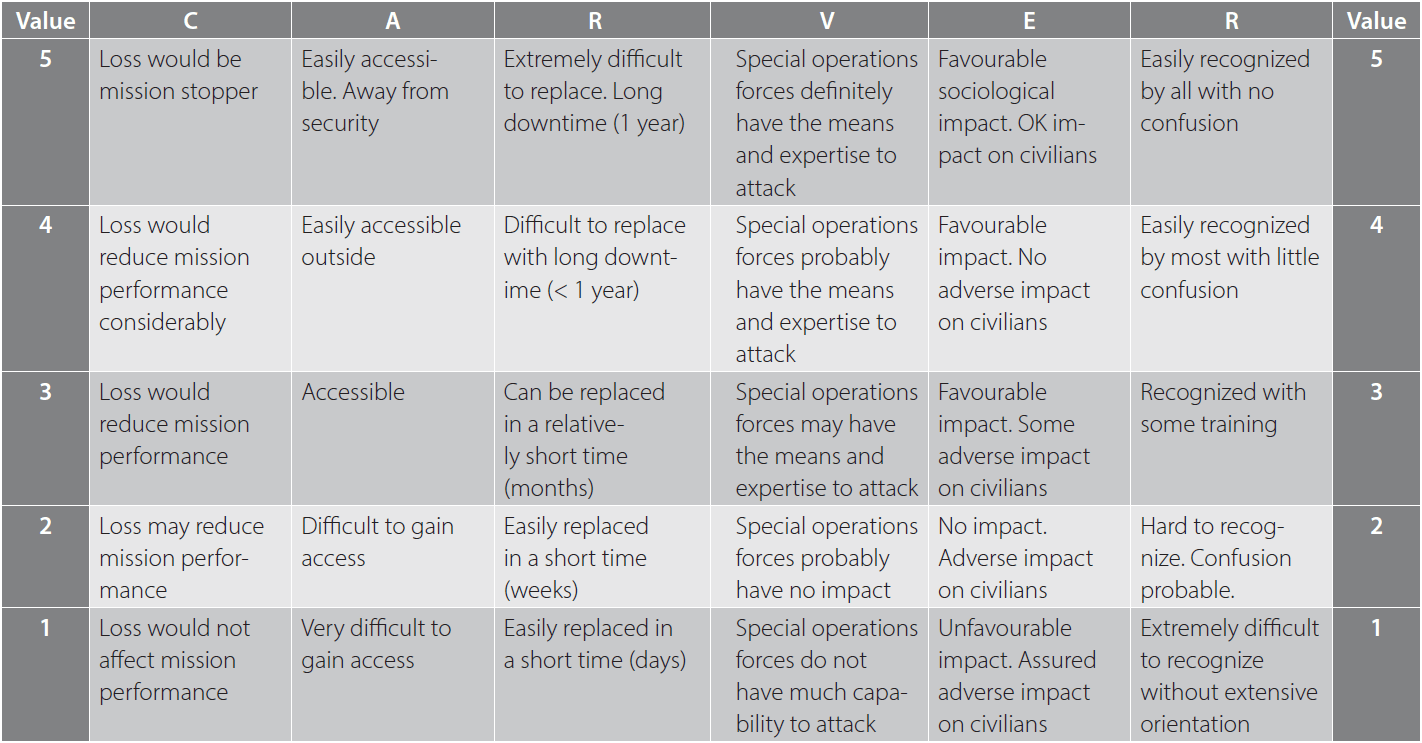
Target Systems Analysis (TSA) is a system to identify and rank specific targets and their elements so that attack resources can be efficiently used and the most vulnerable element or critical link within a system can be targeted to neutralize the system or unit. Should the TSA determine that the data link is the most vulnerable element, for example, in the analysis of the overall system of larger military UAS, then this would be a focus area for intel gathering and planned attacks on that particular element of the overall system. Should the analysis determine that data links are the focal point for neutralizing the UAS threat, then there will be many factors considered (i.e. vulnerability of satellite links, the satellites themselves, remotely stationed satellite receiver stations, the mitigated risk against one’s own forces in attacking this particular element, whether lethal or non-attributable non-lethal action is required, recuperability, etc.)
There are many examples of how to conduct an analysis and the CARVER method is just one example. CARVER is an acronym for attributes used to evaluate a particular target and help in identifying critical elements:
- Criticality. A measure of how critical a node is.
- Accessibility. The ability to physically access and egress from a target.
- Recuperability. The ability of a system to recover from an attack.
- Vulnerability. The ease of accomplishing an attack.
- Effect. The amount of direct loss from an attack.
- Recognizability. The ease of identifying a target.
From its origins during World War II as a method of quantifiably selecting possible targets for interdiction, it has since been refined and was used extensively by the US Special Forces during Vietnam.
Example CARVER Methodology for Larger UAS
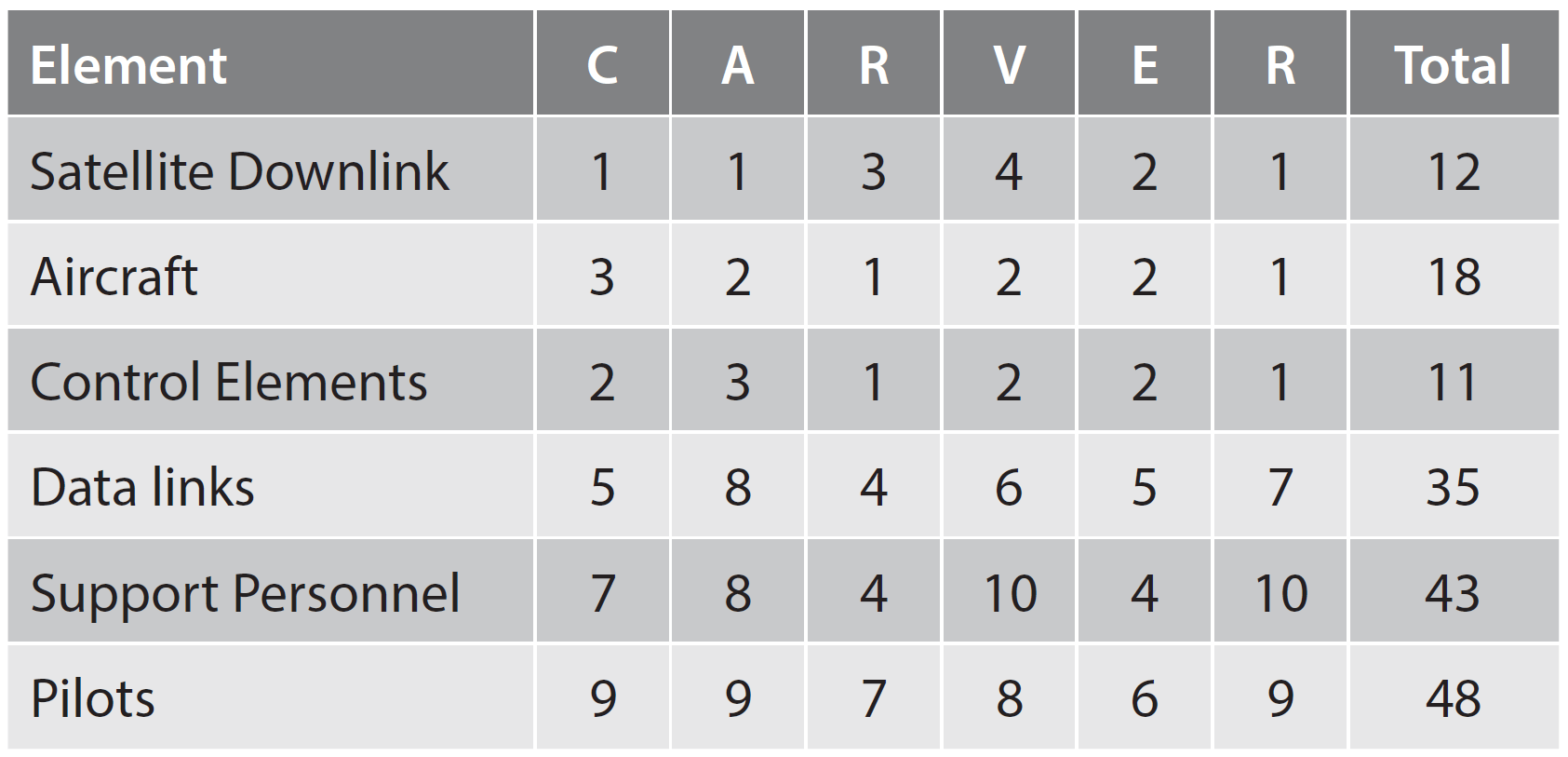
The figures are an example only, but the weighting against the system as a whole by targeting the pilots as a vulnerability would be suggested. Where do the figures come from and what do they represent?
To develop this thought further and to highlight the difference between the different types of UAS, from a targeting perspective, the following targeting details could be considered:
Larger Drones / Formed Military Units
Conducting a TSA on larger drones would focus on the reliant support elements, support staff, data links, communications, susceptibility to electronic attack and the protection of the physical UAS themselves. These elements make up the system of the UAS/unit which could be systematically exploited through several means, and the targeting process determines which element is the most critical and/or takes the longest to reconstitute, whilst minimizing risk to friendly forces.
Target Systems Analysis – Larger Drones
There are many different types of drones, but many of them have similar components that make up their ability to operate (i.e. the aircraft, the payload, control elements, data links, their human operators and support elements). These are not exclusive, nor does every element relate to every drone, but they serve as common reference points from which to build a defence against such technology, from a targeting point of view, and will also suffice as a focal point to start offensive operations. Countering UAS relates to defence from UAS rather than the targeting of them, but there are aspects of offensive action that can be taken against those systems. The methodology to be applied should recognize that whilst there are many drone systems, there are also many similarities that can be exploited or protected against. These include:
- Aircraft have always been most vulnerable when taking off and landing. They are less manoeuvrable, slower and easier targets. Countering drone attacks at this point can easily identify hangars and aircraft parking areas for conventional targeting. The TSA would identify aircraft/hangars as an element of the overall system and weigh the benefits of targeting these facilities. Failure to target these facilities when their location is known and the capability exists would be a wasted opportunity. Factors will be considered which include reconstitution time, and it will measure the effectiveness of the reduction of the overall force should this element of an enemy’s UAS be destroyed.
- Control Elements are integral to all remotely piloted systems. The disruption of the signal that controls UAS systems is where this section is focused. Hacking into systems is not unusual, rather it is a low-attributable offensive act that is becoming more of a remote battleground in the ‘grey area’ of operations. While it could be argued that modern military systems are well protected from hacking, there is a lot of information to the contrary. Only last year (2019), at the Def Con Cybersecurity Conference in Las Vegas, a team of highly-vetted hackers succeeded in hacking and sabotaging the flight system of a US military fighter jet.6 This ‘grey area’ of counter-military operations is effective when targeting a known source or threat, but this is not always the case. Control elements include both the C2 elements in addition to the actual controlling stations. A TSA will identify these and weigh the pros and cons of an attack against this element, but it might also have a different weighting dependent on the means of attack.Formed-military units and the location of control elements/C2 elements would expect to be sourced through intelligence for an attack to take place. However, this could result in a conventional or cyber-attack, which would have a different weighting within a TSA. For larger UAS, employing cyber is not without precedent. The US RQ-170 Sentinal UAS, which was captured by Iran in 2011 was ‘supposedly tricked into landing where it thought its actual base was in Afghanistan, but instead, it was made to land in Iran’.7 The Iranians allege ‘reverse engineering techniques that they had developed after exploiting less sophisticated American drones captured or shot down in recent years. They were able to figure out how to exploit a navigational weakness in the drone’s system’.8 The inclusion of mobile targets, such as a UAS would be complicated within a deliberate targeting cycle. Tacticians may never know where UAS will be in advance, but a dedicated operation to capture something, similar to the example above, by a land unit would be dependent upon having local tactics to execute.
- Data Link is an area that also involves the control elements. Communications are essential to the control of UAS and have been targeted in the past, primarily due to the vulnerability of the link itself. There are many instances where data links have been targeted to gain control or bring down a drone. From a military perspective, an electronic attack on a known location could be an avenue for C-UAS targeting. While the technology is in its infancy, there is the potential for an Electro-Magnetic Pulse (EMP) aimed at disrupting data links for UAS as a means of defeating a threat. Conversely, there is nothing to prevent the same technology from defending critical infrastructure. Drone Defender Technology from Battelle9 and Epirus, Inc.’s Leonidas10 are examples of such technology.EMP causes electric potential to build up in exposed circuits, and because of its power, Electro-Magnetic (EM) shielding does not help protect a UAS design. Induced electric potential is a very high negative charge and travels as an electric current through conductors where the current is high enough to knock out electronic components in its way. As Commercial off-the-Shelf (COTS) drones necessarily use sensitive low-power electronics and require an antenna to function, an EMP will likely destroy all the drones’ electronic circuits. The small proportion that are not destroyed outright would potentially be incapacitated by having their radios destroyed. Whether an EMP would have the same effect on larger UAS is a matter for further investigation.
- Support Personnel. For military UAS pilots, their lengthy and high degree of training makes them equally vulnerable to multiple threats. This can range from coercion and other non-lethal threats through to individual lethal targeting. The vulnerability of personnel, who have freedom of movement is well known and tracked by foreign intelligence services. Anywhere along the path of daily life could be a potential location for a conventional attack, but coercion is becoming more of a weapon against individuals who have something to hide or be embarrassed about. Even the fact that they have been approached is potentially exploitable as it pits one person’s word against another as to what has been discussed and agreed, or not.
Smaller Commercial off-the-Shelf UAS
Smaller COTS UAS have a limited range and are small enough to go undetected by regular radar defences. They are made up of a controller and a drone, are highly manoeuvrable, and can appear without notice. All of these factors highlight a wholly different area of focus for C-UAS than that which would be considered for larger drones. The targeting of these systems requires a different approach.
UAS have developed considerably in recent years. So much so that the smaller types are becoming more affordable and are more readily available for use by non-State groups, organized crime syndicates and terrorists. This will increasingly become a matter of concern for all countries and alliances when considering threats to personnel and infrastructure. There have been numerous attacks of this nature that have had varying levels of success, but one thing has been constant regarding the nature of this offensive thinking, and that is the limited development in the way of a defence against low and slow UAS threats from a military standpoint.
Target System Analysis Smaller Drones
In conducting a TSA against this type of UAS, different factors would be considered. It should be noted that:
- Electronic Defences. Many modern drones have been built with digital ‘gaps’ that can be easily exploited, with security often overlooked in the struggle to satisfy public demand for drones. If the threat against modern-military systems is so easily purchased ‘off-the-shelf’, then these vulnerabilities will be commonplace amongst those threats.A study by Johns Hopkins University identified three successful hacks that were easily achieved on a common hobbyist drone.11– The first hack focused on bombarding the UAS with thousands of wireless connection requests asking for control of the airborne device, overloading the Central Processing Unit (CPU) and causing it to shut down.
– The second hack sent the UAS an exceptionally large amount of data exceeding the capacity of the buffer in the aircraft’s flight application.
– The last focused on sending repeated signals to the drone’s controller, telling it that it was the drone itself. Eventually, the controller started to believe that this was the drone and severed contact with the actual drone.Whilst these hacks were conducted in a controlled environment, one can easily see how these hacks could be further exploited with little additional effort. Identifying the location of the UAS control station and the ranges required to have an effect notwithstanding, it is an area that could potentially focus on countering inexpensive, COTS UAS threat that is present today.
- Control personnel are a vulnerable element of a UAS system and would often be hidden from sight or acting remotely when carrying out a drone attack. Distances vary, but with smaller cheaper systems, it is reasonable to assume that there would only be a small radius of operations from the controller to the drone. Constant Hawk12 is a Wide-Area Motion Imagery System and feeds intelligence data collected in order to understand the environment. It is not a new system and, as the article explains, was used extensively since 2006 in both Iraq and Afghanistan to counter roadside Improvised Explosive Devices (IEDs). More than just Full-Motion Video, monitoring an area surrounding a vulnerable target using this technique has the potential to capture an area of approximately 100 sq. km for constant surveillance. In either real-time or when reviewed at a later stage, following the footage back from an identified launch point/impact point can lead authorities to the location or origin of the actors involved, the building that they operated from for example. Those control personnel can then be individually apprehended or targeted through the normal targeting cycle.
The legalities of this type of targeting would be considered at the time, but the differences between legal targeting and self-defence against this type of threat will be an area for consideration, especially when the perpetrator is a local civilian, and you cannot argue self-defence unless an attack has taken place. The thing we are countering is the perceived attack itself. With that legal issue notwithstanding, and with the example of Constant Hawk in mind, there is a means through intelligence to positively identify and track offenders who may otherwise blend into and hide within local society.
There is a very noticeable difference in the countering of these two different types of UAS, where one is detailed and planned action against a known system that has had a vulnerability identified, while the other is reactionary to a hybrid-type threat to critical infrastructure or personnel. In the case of the latter, then an analysis of the known factors surrounding these types of attacks and utilizing a full coverage of Intelligence, Surveillance and Reconnaissance (ISR) will best enable a defence, along with indicators and warnings, to this growing threat. Having completed a TSA, regardless of the type involved and analyzed what primarily needs to be targeted in a UAS threat would then form the basis of a defence.
Recommendations
The threat to governments and businesses in modern times is so substantial that there are companies that specialize in C-UAS technology, not only for the military and the terrorist threat that exists in modern-day warfare, but in the civil sector itself. One such company, for example, is the German-based Frauenhofer whose Chairman states ‘…drones that can carry explosives, self-sufficient delivery drones, self-learning drone swarms – and the materials required are available in every hardware store’.13
Many readers with interest in this subject will be aware of the Slaughterbot demonstration on Youtube of autonomous drones searching for targets. Their parameters are defined by facial-recognition technology and social media. It is a fictional demonstration of what potentially could be utilized should drone technology be used for terrorist purposes or even uncontrolled-military purposes.14 The video was released by autonomousweapons.org and Stuart Russell, a Professor of Computer Science at the University of California, who speculate on the potential of Artificial Intelligence (AI) and in particular, drone technology. If what the Chairman of Fraunhofer states is true, then this technology is available and awaiting exploitation. Utilising drones from an offensive point of view was clearly demonstrated by Stuart Russell and it would be reasonable to expect that it is only a matter of time before this type of attack is commonplace.
Conclusion
It is clear that we are breaking new ground when it comes to countering this type of threat to a modern military force. There are many threats to protect against and many aspects with potential for exploitation. If this new and emerging technology is to be recognized for the threat that it is, particularly the more frequently used non-traditional and hybrid means, then it could be argued that there should be doctrine to give guidance for the protection and future development of C-UAS. This is a cheap, affordable, non-attributable means of conducting a stand-off attack against infrastructure and personnel of importance. The examples thus far of dedicated lethal attacks are limited, but as the technology develops further, the capabilities of newer threats may leave us feeling more vulnerable than we first thought. The reluctance of governments to accuse third parties, due to this non-attributable means of attack, will only bolster and encourage future exploitation through these means.












