Introduction
Unmanned aircraft (UA) are an established technology that continues to expand. Over the past decade, UA have become an integral component in most militaries and future military operations must consider Friendly-UA (F-UA) and Opposing-UA (O-UA) capabilities. It has to be assumed that O-UA have similar capabilities to F-UA, able to deliver kinetic and non-kinetic effects in addition to Intelligence, Surveillance, and Reconnaissance (ISR). Therefore, O-UA actions must be planned for in all operations, including considering contingencies. As described in Chapter 7 (cf. p. 107 ff.) about the role of Surface-Based Air and Missile Defence (SBAMD) systems, there currently exists an initial capability to target the majority of Unmanned Aircraft System (UAS) components individually. In addition to SBAMD, manned aircraft performing Defensive Counter-Air (DCA) missions train to engage larger UA in the Class II and Class IIIi categories, however, both of these defence assets are scarce resources within NATO and Counter-Unmanned Aircraft Systems (C-UAS) is just one of their many requirements. In order to augment relatively limited SBAMD systems and DCA aircraft, F-UA have the potential to be an excellent C-UAS platform for many scenarios. The following paragraphs will look at F-UA applications for the C-UAS mission. Once these applications are described broadly, the paper will address how F-UA may be employed to defend against O-UA conducting DCA and Offensive Counter-Air (OCA) missions.
In an attempt to counter opposing unmanned aerial systems, friendly forces may target anyone or many of its critical system components (cf. Figure 1.1, p. 13).
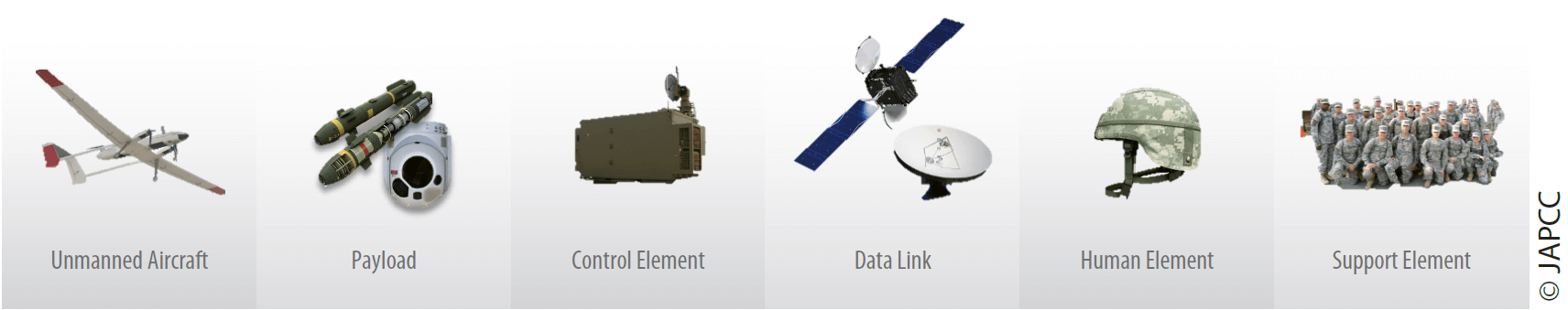
Although there is work being done to build a capability to target components other than the UA,1 Allied tactics currently focus on targeting the O-UA with SBAMD and manned DCA aircraft at ranges that are sufficient to prevent the O-UA from completing its mission. Since this approach relies upon defeating a single component of the UAS, which is also the component that often has a large number of required targets, this approach may be considered inefficient compared to targeting more critical components such as the C2 element or the data link. Hence, after discussing the challenges of targeting O-UA, this chapter will expand on countering the other components of the opposing UAS by utilizing F-UA for OCA missions.
Detecting the Unmanned Aircraft
Detecting the threat is the first link in the kill chain. Surface-based detection assets such as active radars and passive receivers are generally very powerful and work well to detect Class II and III UA. The primary deficiencies of using ground-based detection assets are that they are susceptible to target terrain-masking (blind zones) due to topography and that they are also relatively slow to redeploy as compared to O-UA and other manoeuvrable enemy forces. Detecting the target from an airborne asset can greatly reduce these issues. Although manned aircraft are capable of executing the C-UAS mission against Class II and III UA, there are many reasons to look at using F-UA for C-UAS missions. F-UA are more tailorable to specific mission requirements in terms of size and function, including options that, due to small physical size, could not carry a human. In addition, unmanned platforms can be tasked for higher risk missions in that they are perceived as more expendable. F-UA employed in tactically advantageous positions, with active or passive sensors, would be able to substantially reduce blind zones in the coverage provided by ground-based sensors. Additionally, F-UA have the potential to deploy and reposition as required to counter adversarial manoeuvres much more quickly than ground-based detection systems. In addition to those advantages, UA create the potential for more effective, highly-automated tactics to be employed through the use of artificial intelligence and machine learning. Vulnerabilities of UAS include the requirement for multiple data links that need to be maintained at various levels (which can be exploited), in addition to smaller antennas and substantially less energy available for transmissions as compared to ground-based assets (especially for Class I and II UA). The optimal solution to enable O-UA detection is likely a combination of tactically placed ground units augmented by the appropriate number of F-UA sensors, based on the topography and size of the area being defended.
Classifying the Unmanned Aircraft
Once a potential target is detected, it must be classified and identified, based on Rules of Engagement (ROE) and supplemental plans and procedures to determine the correct response. This determination is so critical in the kill chain that automated classification is often a concern due to trust issues as well as legal, moral and ethical principles. Although many nations are comfortable with machine derived classifications2, they require these systems to be supervised by human operators who interpret the complex tactical and strategic situations to determine the classification. Although this current approach may reduce the occurrence of collateral damage and fratricide, there are some obvious drawbacks. The first drawback to requiring humans in the classification process is that in future scenarios, with fast-paced operational tempos, humans could slow down the decision-making process, hence decreasing effectiveness. The second is if communication is lost from the forward-deployed UA, the human commands would not be issued to the UA. With fully-automated classifications allowed, F-UA may be able to classify the contact as hostile and work with other assets to neutralize the threat in situations that necessitate quick actions. The level of human control over UA classification systems in the future must continue to be evaluated to weigh the risk between fratricide and failure to provide adequate defence from a credible threat.3
Engaging the Unmanned Aircraft and Payload
Once a contact is classified such that it can be engaged, the appropriate actions to neutralize the threat need to be determined. Again, surface-based solutions have the potential benefit of having more capable defences such as long-range interceptors or high-power directed energy weapons. As previously mentioned, blind zones and relatively limited manoeuvrability can be supplemented by F-UA to mitigate the gap and to create a layered defence. When defending against O-UA, especially swarm and emergent attacks, the use of F-UA is desirable as they are more plentiful, agile, and likely cheaper than traditional air defence assets. The use of F-UA could also lead to optimized weapons for C-UAS, including a self-destruction option that involves directly impacting O-UA.4 F-UA may provide a better defence as compared to manned aircraft, especially when the mission requires long ‘on-station’ or dwell time or necessitates operating in highly contested airspace. In addition, the flexibility of F-UA allows for air operations to be conducted in areas with limited access to logistic support, where conducting manned flight operations isn’t feasible. Synchronizing the use of unmanned and manned assets, while prioritizing the unmanned assets to complete the most hazardous missions, will allow for more creative, flexible, and effective engagement solutions.
It is always preferable to engage offensive aircraft before they are able to release their payload since this approach is more efficient and survivable. In most cases, the offensive aircraft will release multiple individual weapons that may be more difficult to engage than the aircraft itself, in addition to the reduction in available friendly response time once the weapon is employed. If weapons are released, then F-UA may be critical to the survival of the defended asset. Utilising characteristics of UA already discussed, they could be positioned in tactical locations, supplementing existing manned defences. If adversarial tactics involve saturating friendly defences with a high number of weapons, F-UA may be employed as a flexible response in numbers sufficient to negate the threat. When large numbers of credible threats need to be prioritized and eliminated quickly, high-automated defences could be the most survivable option and will be discussed next.
Acknowledging known concerns, engaging all threats (both hostile aircraft and incoming weapons) through highly-automated systems has many advantages. With a high concentration of threats executing complicated tactics and composed of a variety of weapons, a properly monitored autonomous system may be the best solution. A highly-automated architecture may be more effective at managing the Command and Control (C2) of vast friendly offensive and defensive systems simultaneously than human-in-the-loop systems. Legal and ethical concerns remain within many nations when employing any effects without human consent.5 In addition, highly-automated C-UAS C2 systems will need to be interoperable with all other overarching and potentially coexisting C2 systems.
Employing Friendly-UA for the Defensive Counter-Air Mission
Defensive Counter-Air (DCA) operations protect friendly forces and vital interests from adversary air and missile attacks. It consists of all active and passive air defence operations to detect, identify, intercept, and destroy or make ineffective, adversary air and missile forces attempting to attack or penetrate friendly airspace.6 In a typical DCA scenario, a high-value asset (mobile or stationary) is defended from threats originating from a specific direction. Many aspects of a typical DCA mission indicate UA may be well equipped to fill the defender role. These aspects include relatively short distances for communication and support, with F-UA either prepositioned or launched upon threat detection. For example, if the threat is assessed as capable of launching an O-UA swarm attack with little friendly indication and warning (I&W) capacity, F-UA assets could be placed in multiple layers along the threat sector in order to provide layers of defence as well as relaying initial indications of the threat to follow-on layers. Forward deployed positions of F-UA also offer the opportunity to detect and engage from behind the attacking aircraft once the attacking aircraft has passed their location and are be-tween the F-UA and the defended asset. Considering that the majority of low observable technology (which will also be incorporated into future O-UAii) concentrates on reducing detectable signatures in an aircraft’s forward quadrants, having F-UA able to detect (and potentially engage) from the rear quadrants could greatly improve overall air defence capabilities.
Employing Friendly-UA for the Offensive Counter-Air Mission
Offensive Counter-Air (OCA) consists of offensive operations to destroy, disrupt, or degrade adversary air and missile capabilities, either before or after launch.7 With regard to C-UAS, this involves the enemy’s ground control stations and satellite ground terminals as well as other communication nodes. Moreover, it includes all the logistics and supporting infrastructure which is necessary to operate O-UA. Therefore, a typical OCA mission will involve friendly missiles and/or aircraft entering contested airspace in order to engage enemy aircraft and missiles in their own territory. OCA by manned aircraft in support of C-UAS is also discussed in Chapter 8 (cf. p. 129 ff.). An OCA mission can be characterized as involving longer flight distances than typical DCA missions, which may be more of a challenge for small, inexpensive F-UA. Typical inexpensive UA have somewhat limited range and speed in addition to substantial vulnerability to EMS jamming, since they are utilizing less secure or even unprotected data links for mission accomplishment than larger, more expensive UA. A possible solution to these limitations could be enabling the F-UA to proceed autonomously after launch (minimizing the consequences of EMS attacks) in addition to planning ‘one-way’ missions where the entire range of the system can be utilized without saving fuel for the return trip. These kinds of missions could enable F-UA OCA missions to be effective at degrading O-UA capability before they can be used against friendly forces.
One concept for employing F-UA8 while optimizing logistics and minimizing costs for the OCA mission is to utilise ‘plug-and-play’ payloads in a standard F-UA airframe and employ them to create synergistic effects. The type and number of mission-configurable F-UA platforms would be determined based on anticipated enemy defences and desired effects, similar to today’s (manned) Composite Air Operations (COMAO) strike planning. F-UA could supplement or completely replace manned aircraft for certain missions within the OCA package. For instance, instead of sending multiple manned Airborne Electronic Attack (AEA) aircraft along with manned escort aircraft to provide Suppression of Enemy Air Defences (SEAD), an OCA package could utilize F-UA configured for the AEA mission to accomplish the task. With potentially a larger number of F-UA available to complete the SEAD mission, combined with being able to assume more risk to adversary air defences (able to operate in more contested airspace and without escort aircraft), F-UA may prove to be a much better solution than the current manned options. The challenges to this kind of coordinated attack include strike planning with assets possibly having large differences in transit speed and other characteristics. However, considering the benefits of using F-UA for other missions within the COMAO, it’s feasible to imagine an OCA package being made up completely of (mission-configurable) F-UA at some point in the future. The majority of the F-UA in the COMAO could be designed from the same basic UA but loaded with mission-specific interchangeable payloads and connected to a sophisticated C2 system. The F-UA could be programmed with contingency plans, including various levels of lost communications. If the link to human monitored C2 was severed, the COMAO could be programmed to make decisions autonomously based on shared information within the ‘swarm’. If the inter-flight link was severed, each F-UA would individually execute their lost-communications contingency orders, tailored to the tactical scenario. The future degree of human control required for large scale operations, such as COMAOs, should continue to be evaluated based on the level of trust of the systems being employed and acceptable risk to unintended actions of these systems if automated.9
F-UA for Self-Defence
F-UA may be well suited to help defend systems and personnel from O-UA in a self-defence scenario.10 O-UA have the potential to be employed against aircraft from short distances and with little warning, especially when the location of the manned aircraft is predictable due to the use of standard air routes and regularly scheduled missions. For example, O-UA could be employed under airport approach corridors or near frequently flown paths such as low-altitude training routes. Rotary-wing aircraft are especially vulnerable since they are typically slower and lower than most fixed-wing aircraft. In addition to air assets, ground-based assets are also vulnerable to no-warning attacks, when their future locations are predictable. Even if some level of early warning is available, it seems feasible that specially designed O-UA could be capable of defeating most layers of friendly defences. It is reasonable to assume that F-UA could be highly effective in providing self-defence, in a similar fashion to traditional expendables such as chaff or flares that are used in a final attempt to defeat an incoming weapon. If a threatened asset, from a major weapon system to an individual soldier, senses an O-UA attack, they could employ their own UA in self-defence. Self-defence F-UA is not the only solution to C-UAS, but should be considered as a complement to other defences and could provide a very versatile and affordable option. For example, ‘Hunter’ F-UA which are capable of catching O-UA and safely manoeuvring them to a safe spot, could also augment the perimeter of Short-Range Air Defence Systems if the ROEs are very restrictive and collateral damage or public safety is a concern.11
Engaging the C2 and Operator Elements
One significant benefit of unmanned systems is that the C2 element and operator are not primarily affected by the destruction or detection of the UA itself. Deploying a new UA restores full operational capability. The C2 component is not as redundant as other components (such as the UA), which makes locating and neutralising them paramount. In the case where the C2 element is controlling the UA via RF transmissions, the C2 element or transmission hubs may be located by passive RF detectors. F-UA are especially qualified to perform the detection mission, since their elevated position enables them to detect transmissions over a wide field-of-regard and they can provide target location via triangulation. Additionally, once transmissions are sensed the F-UA may be able to call for additional F-UA in order to obtain more precise triangulation coordinates or execute a coordinated mission.
Engaging the Data Link
Having already discussed how F-UA may be used to defeat the other components of an adversary’s UAS, F-UA could also be used to target the data link and other communications between the UAS nodes. The effects of the attack could result in data link denial or manipulation of transmissions to disrupt their operations. These kinds of effects may be easier to achieve on traditional omnidirectional emitter-receiver systems, but they may also be possible for directional communication links. Especially with agile F-UA, it could be feasible to position them in between the O-UA and its C2 element or relay hub. Even when the data link is relayed by satellite, a very high-altitude UA (also known as Pseudo Satellites) might be able to cause the same effect.
Summary
Unmanned platforms show significant promise in conducting effective C-UAS operations in conjunction with surface-based and airborne manned platforms. F-UA are able to complement or supplement existing efforts to defeat the individual components of an adversary’s UAS, while also bringing new capabilities. The use of F-UA has the potential to dramatically increase overall C-UAS capacity while increasing survivability of manned offensive and defensive assets. Since all future adversaries, from small terror organisations to peer competitors, are currently using or plan to use UAS, a reliable, modern, and robust set of answers needs to be developed. Due to the wide variety of UAS and potential missions, C-UAS will also require a comprehensive range of counter-techniques. During this analysis, the level of automation afforded to human-machine-teaming must be considered, including balancing the operational, ethical, and legal aspects.













