Translated by Lieutenant Colonel André Haider, GE A, JAPCC
Introduction
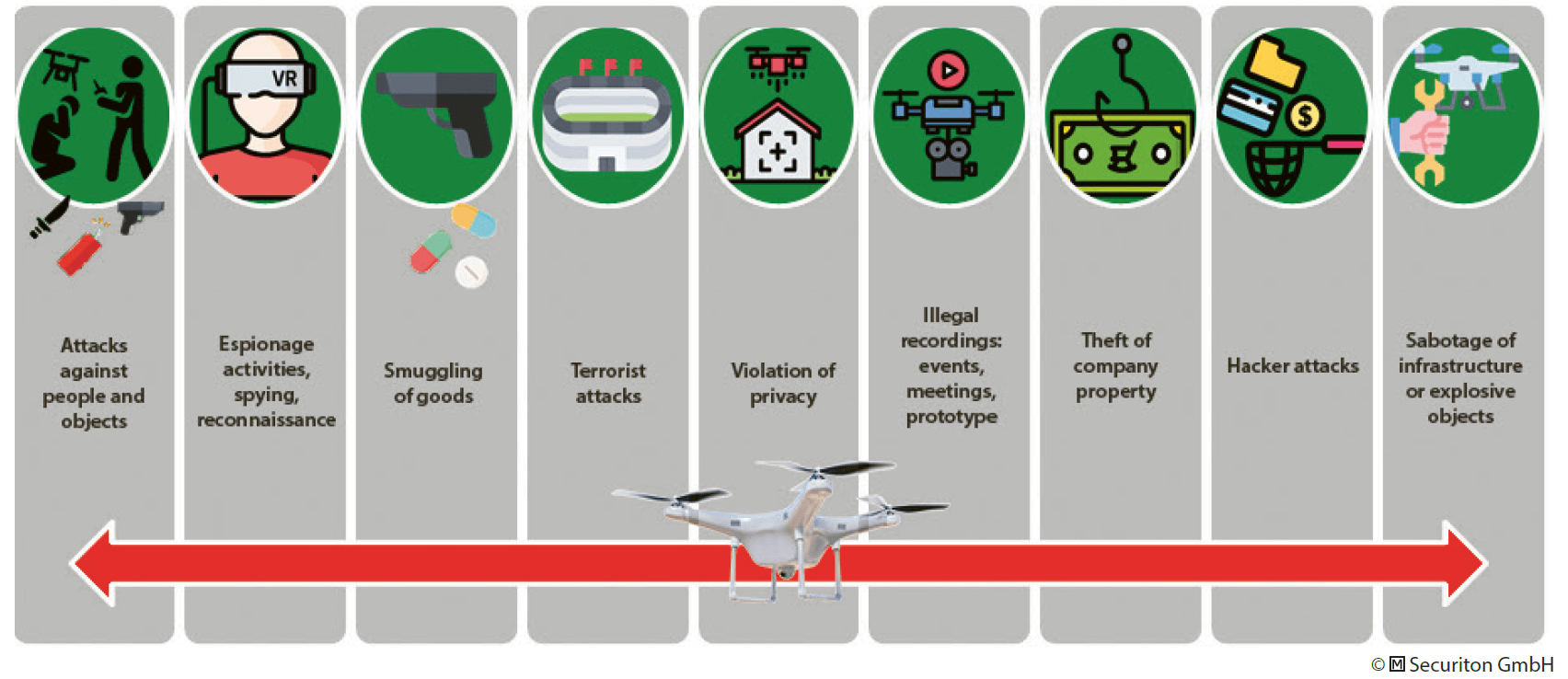
Small drone systems for private and commercial use consist of many high-tech components, offering many useful new applications for the public. However, drones are also ideal instruments for criminals and terrorists to considerably expand their capabilities. An effective defence against drones which are operated with malicious intent is therefore likely to require a similar approach utilizing sophisticated counter technology.
Today, drones are readily available to anyone and are becoming increasingly powerful. The potential, and with it the frequency, to harass, endanger and commit criminal or terrorist acts with the help of drones is constantly increasing.
Drones allow offenders to act quickly and undetected, thereby minimizing their risk. At the same time, it is not easy for a victim to recognize a drone and immediately assess its intentions. The sudden and unexpected appearance of a drone, in the vicinity of critical infrastructures or protected persons, should generally always be considered a malicious use of a drone.
How can one protect themselves from such surprises? Are there countermeasures that are about as expensive to purchase as drone systems and that can be used swiftly and readily in any given area of application?
Traditional Protection Measures
Historically, castles or strongholds were erected (structural measures) and guards were stationed (organizational measures) to protect property with valuables and to safeguard key persons. If an important person had to leave the castle or precious materials had to be transported, they were usually accompanied by a reinforced guard force.
Today, in addition to fences, walls and protective armour, technical equipment such as fire alarms, intrusion detection systems, video security systems (technical measures) are used as aids for access control, security guards and response teams to protect critical infrastructures. The organizational measures comprise risk analysis as well as contingency plans to avert and limit damage in the event of any threat.
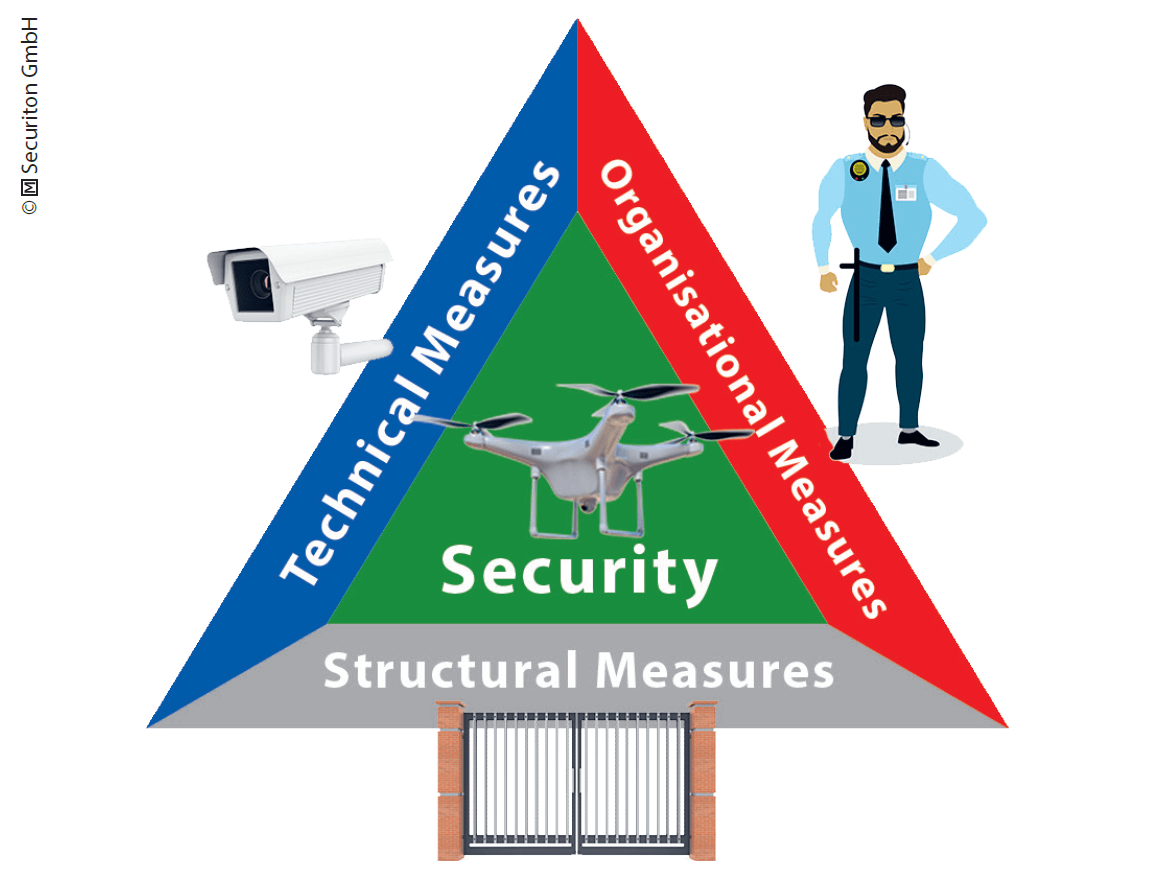
The highest level of security against potential threats can be achieved if all three of the above-mentioned groups of measures (cf. Figure 20.2, p. 353) are properly coordinated.
A feasible, yet cumbersome method, to protect against a drone attack, is placing people and property inside a building (shelter) and to close all entrances and windows. However, hardly any structural measures are feasible against airborne drones in the open. Organizational measures, like security guards performing airspace surveillance, are also largely ineffective against small drones, since their size, speed and mobility overstrain human eyesight, especially in the closer vicinity.
Therefore, countering drones can only be achieved using specialized technology in conjunction with the appropriate organizational provisions. It should be noted that drones may also be used while key persons are travelling, valuables are being transported, many people are gathering at one place or while valuables or critical materials are temporarily stored in the open.
Drone Protection Technologies
A technology for protection against drones should be as fast and as user-friendly as possible and be applicable everywhere, just as one or more drones can be used quickly, easily and at any place.
Drone Detection Methods (Sensors)
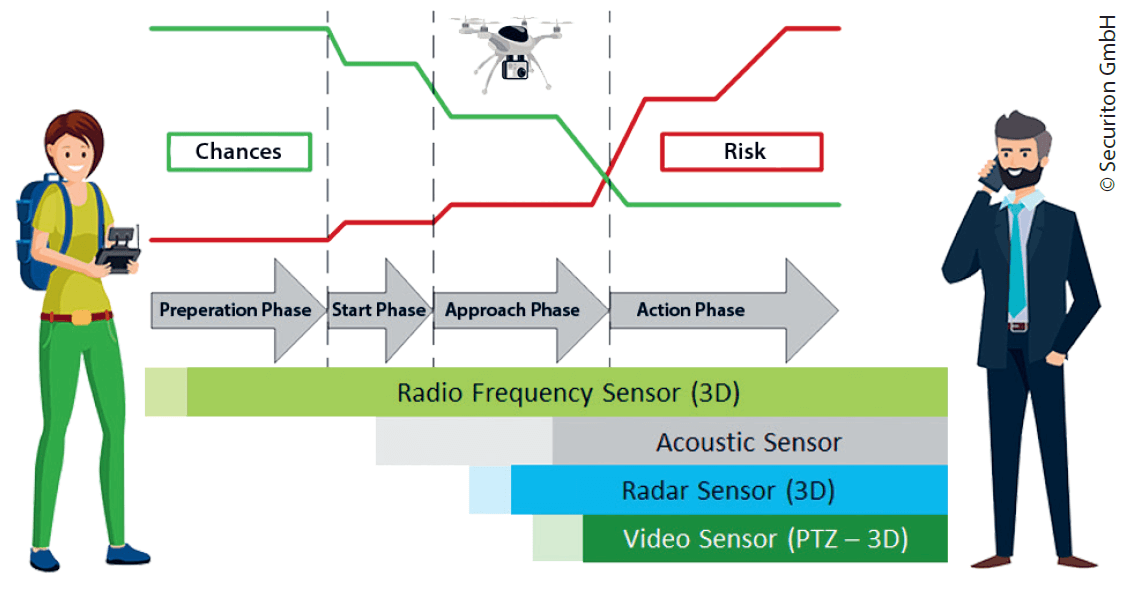
To protect against drones, it is first necessary to detect them. This requires sensors like:
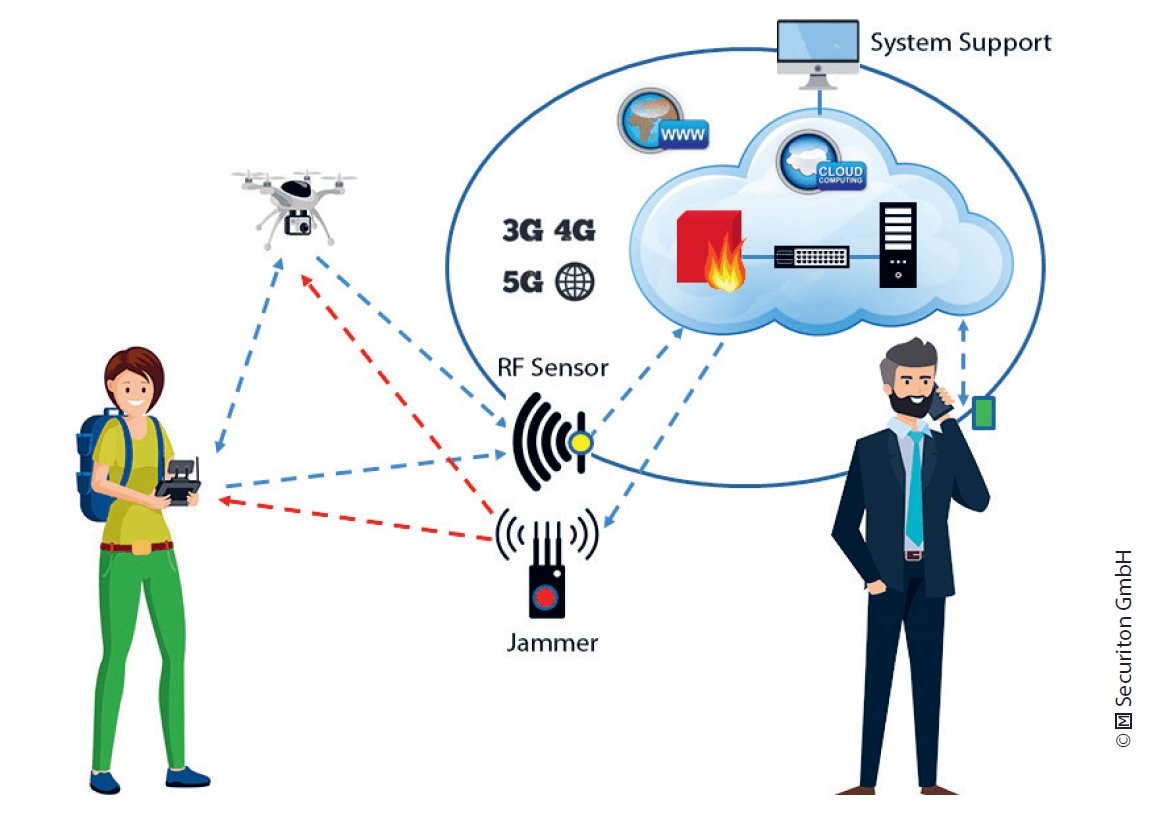
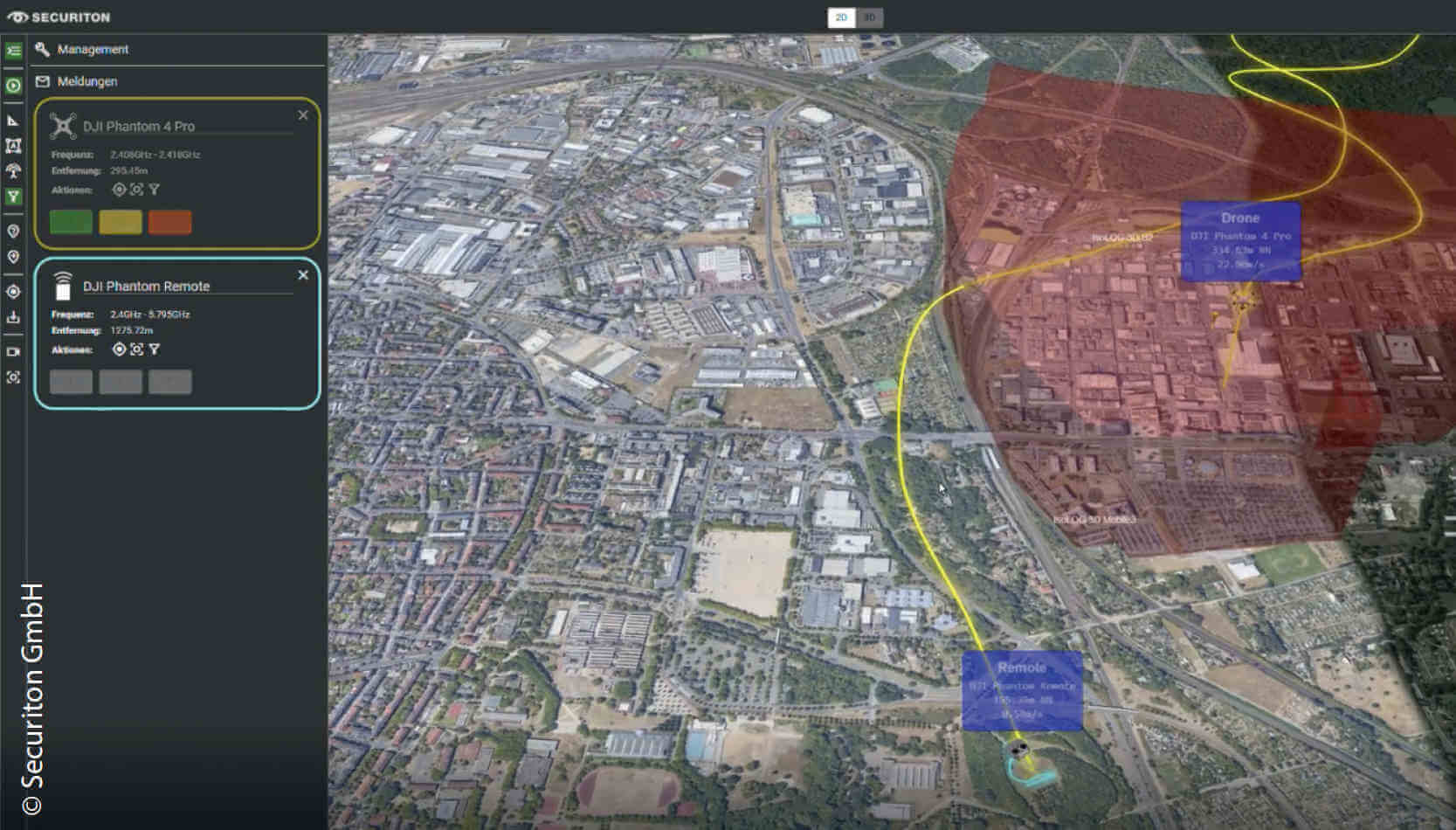
Radio Frequency (RF) Sensor: The RF sensor is a Beyond Line-of-Sight (BLOS) sensor that can detect drones and drone remote controls at great distances and distinguish their transmissions from the overall radio spectrum. It is the only sensor that is capable of detecting drone operations in the preparation phase, as soon as a remote control unit is activated. Smart RF sensors capture the content of radio transmissions to drones which allows for – depending on the model – identification and display of the drone model, battery charge status and maximum payload of an approaching drone. For accurate 3D target acquisition of drones, an RF sensor must have at least 2 (preferably 3) distributed 3D RF antennas in order to determine the targets’ details (drones and drone controller) by means of triangulation. A single RF sensor can detect a drone at a distance of several kilometres.
Acoustic Sensor: An acoustic sensor is also operating BLOS and can detect the typical noise of a drone’s propellers. However, depending on ambient noise, the detection range may be quite limited.
Radar Sensor: A radar sensor actively transmits RF energy and captures the reflected signals. This mode of operation requires LOS to the target, but it can detect drones at higher altitudes and distinguish them from other flying objects such as birds. A radar with 3D characteristics can also determine the direction to the drone target, its flight altitude and speed. Dedicated radars for drone detection are capable of sensing drones at distances of up to several kilometres. Radar sensors often require approval from the civil authorities to operate, depending on the model and location.
Image Sensor: An Electro-Optical (EO) video camera, often also combined with an infrared (IR) sensor, requires LOS to the drone and recognizes it using image processing, provided that the drone passes the camera’s field of view. Special camera systems with smart video sensor technology achieve viewing angles up to 360°. A camera mounted on a Pan-Tilt-Zoom (PTZ) head is usually dependent on initial target recognition by an RF or radar sensor. However, once a PTZ video camera has locked on the drone, it can follow it autonomously and provide live images of the drone, its cargo and its behaviour. A PTZ high-performance camera with an AI-supported video sensor can track a drone at a distance of several kilometres and still display a recognizable image of the target.
Remote Identification Sensor: This type of sensor detects the Remote Identification (RID) signal transmitted by a drone. In addition to the unique RID, it is foreseen that drones will also be required to constantly transmit their current position, altitude, speed and flight direction. Drones with CE Class C1 – C3 are to be equipped with RID from 01.01.2021 onwards. From 31.12.2022 onwards, RID will become a mandatory standard for every drone, and older systems are to be equipped with it as well. Chapter 21 (cf. p. 375 ff.) covers these upcoming regulations in detail. If drones then have to be registered with the authorities, the registered owner of the drone can be identified through its RID. It is foreseeable that receiving drone RID signals will be supported by cell phones as well. This will enable any private person with the appropriate app to track the drone traffic in the vicinity.
This is a significant advantage not only for airspace surveillance but also for drone defence. Now, all drones have to transmit radio signals during flight and thus are identifiable by RF sensors at all times, even if they operate autonomously or on a pre-programmed flight path. Additional information about the drone can be obtained immediately once the RID transponder is in place. Drones without RID can then be distinguished from RID-compliant ones, and special attention can be paid to them.
However, even today’s drones without RID, which operate autonomously or pre-programmed typically still send radio signals back to the remote control and thus are detectable by RF sensors today. This is especially true when on-board cameras transmit their video signals to the operator’s screen. Hence, since almost all drones and their remote controls emit radio signals, RF sensor technology for the detection of these systems should always be considered as the primary sensor option. Simple yet powerful RF drone sensors are already available on the market for a reasonable investment.
In the unlikely case of a drone operating completely autonomously and without any emission of radio signals or RID, this drone needs to be treated like a flying object without a predictable flight path. For this purpose, other sensors such as radar, acoustics or video must be used in addition. However, as a general rule, more than one sensor should always be used for reliable drone detection.
Drone Defence (Effectors)
Having to counter airborne drones is literally the civilian variant of the military Air Defence mission. Although the civilian options are limited, there are several possibilities available, which are listed below:
Jamming: Since almost all drones and their controllers emit RF signals, radio interference is the most straightforward and effective countermeasure against small drones. Jamming affects the approaching drone in its communications with the drone controller or its navigation via GPS and will force the drone to initiate contingency measures, which usually leads to aborting its mission. However, interference on public frequencies is generally prohibited and reserved for the civil authorities.
Depending on the jammer, certain frequency bands or only specific frequencies can be interfered with. If the direction of approach and the communication frequencies of a drone are known, it is possible to jam the drone without overly disturbing other radio users. However, it should be noted that some drones can automatically tune the frequency within their used frequency band in case of radio disturbance. Hence, in most cases, the entire frequency band used by approaching drones needs to be jammed.
Locating the Remote Control: Locating the remote control and thus pinpointing the operator of the drone is a highly desirable means of taking legal action against the originator of unauthorized drone activities. However, the time following detection must be sufficient for authorized security personnel to reach the location of the offender while he is still present.
Take over control: The complete takeover of a drone by security forces is feasible from a technical point of view but due to the complexity and potential legal challenges of this countermeasure, it can only be carried out with specialized equipment and only by authorized law enforcement agencies.
Hard Kill: Firing at drones using special weapons with pellets or net projectiles, laser, sound, heat or electromagnetic pulses are technical possibilities for the defence against drones. However, due to the potential hazards to uninvolved parties these countermeasures are restricted, if not prohibited, for private and commercial use and reserved solely for authorized law enforcement agencies, which are then also responsible for any collateral damage caused by their operations.
Intercept: It has already been tested to intercept drones with trained birds of prey, with varying success and always with the risk of injury to the animal used. The more effective way is probably to use sophisticated intercept drones equipped with special sensors and a net to capture small drones and transport them to a safe location. Intercept drones are already available on the market, and due to the lower risk of collateral damage, specially licensed versions may even be authorized for use by the private and commercial sector in the future.
Many variables such as drone size, numbers, speed, distance, flight behaviour, topography, or environmental conditions can have a significant impact on the effectiveness of sensors and effectors used in drone defence. Provided that radio communication is used for almost all drone operations, the influence of the aforementioned factors on the radio frequencies used is minimal. Hence, radio communication is still the primary vulnerability of drone operations, which allows for its detection and countermeasures to be taken.
In contrast to the mere detection of drones, the possibilities for actively defending against them are very restricted for the private and commercial sector. Unfortunately, harassment, threat or even the committing of a crime using drones can currently only be reported to the police, who will then follow traditional prosecution measures to cope with a non-traditional offence. Whether the police will be able to effectively counter drone incidents in the future is currently subject to new legislation, the provision of new equipment for police forces, the intended implementation of RID and registration of drones also supports this objective.
Command and Control
For cost reasons, small drone defence systems do not have dedicated personnel available for 24/7 operations. The reporting of detected threats as well as the activation of countermeasures must be handled via mobile devices such as cell phones or tablets, so as not to have personnel permanently tied to one location, like an operations centre. When a drone is detected, the alarm is immediately sent to one or more designated mobile devices and the person(s) concerned can then decide on any further measures that need to be taken. A minimum configuration of such a small system with a detection range of up to 2 km is depicted in Figure 20.4.
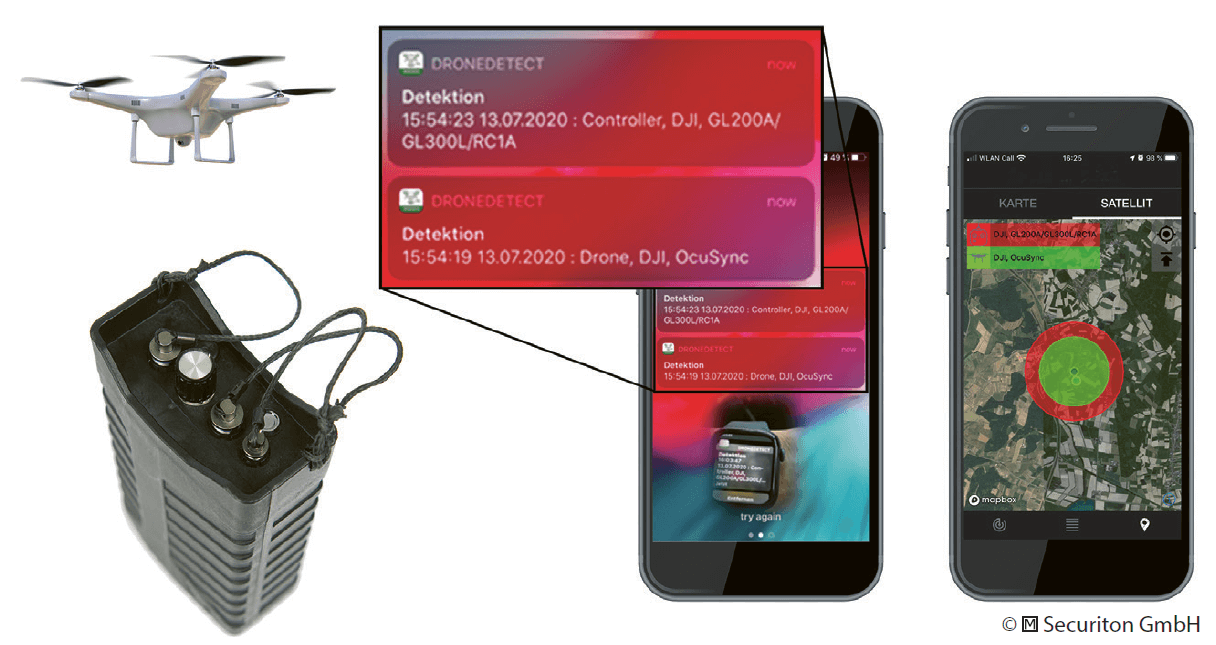
In addition to the small configuration example above, drone defence sensors and effectors can be integrated into any existing security infrastructure as well. Many larger companies have stationary alarm centres established where fire, intrusion and other alarms are centralized. Hence, it seems reasonable to integrate the alarms for unwanted or unauthorized drone incidents as well. The staff on duty can alert people affected by a drone incident, mobilize security forces, report to the law enforcement agencies, or initiate technical countermeasures.
Security Applications and the Internet of Things
The ‘Internet of Things’ (IoT) is a collective term for a global infrastructure of information technologies, which enables physical and virtual objects to be networked with each other and to collaborate through information and communication technologies.
Applications that are implemented with IoT technologies allow interaction between humans and any electronic systems that are connected to them as well as between the systems themselves. Embedded computers, which are continually being made smaller and smaller, are designed to support people without being distractive or even noticeable.
Mobile Monitoring, at its highest level, is the IoT of security technology. Mobile Monitoring is a collective term for temporary surveillance using mobile technical equipment. In this context, the term ‘mobile’ stands for being mobile and relocatable as well as for mobile (cellular) communications. Mobile Monitoring supports security companies and their staff with the surveillance of persons and objects.
Digital video and audio technology, sensors, effectors, GPS, radio systems, mobile communications, the Internet, Virtual Private Networks (VPN), mobile and cloud computing, as well as small accumulators form the basis for mobile monitoring. Many of these technologies are also in use with drone systems.
Of course, (mobile) monitoring systems can also be used for an unlimited period of time in a fixed location to protect infrastructure and personnel. Actually, most of the security systems in use today are located at only one site, and are permanently installed, with fixed cable connections for power supply and data exchange.
Examples of such isolated applications are fire alarms, intrusion detection systems, or surveillance cameras, together with their sensors and effectors. These are connected to a siren and/or a control centre, manned by personnel on 24/7 duty, who initiate the appropriate countermeasures and damage mitigation in case of an alarm.
Drone systems, on the other hand, can be considered an application of IoT technologies as well. Therefore, mobile monitoring must keep pace with, if not stay ahead of, the development of drone technology to provide a comprehensive solution for countering them.
The Advantages of IoT Security Technology
The advantages of networked IoT security technology, especially for drone defence, are:
- Sensors, effectors and devices for Command and Control (C2) that can be deployed swiftly everywhere.
- Temporary or permanent use with mobile or stationary sensors, effectors and devices for C2.
- Plug and play – easy to use with little training effort.
- Suitable for applications in personnel and infrastructure protection as well as for site security.
- Can be networked as required, also with ground-based devices, to form an all-encompassing perimeter protection system against today’s known threats on the ground as well as against the new threats from the air.
- Tailored for client or mission requirements
- Inexpensive in procurement as well as in operation.
- High computing power and plenty of data storage capacity provided by cloud systems in secured data centres. Scalable in any number of sensors, effectors and devices for C2.
- Comprehensive monitoring and logging of all processes and events in data, text, audio, image or video.
- Features such as current 3D position displays and Artificial Intelligence (AI) can be made available across the board.
- Remote operations and support for reporting are possible at any time.
- The most current technology together with the latest system data and configurations of drone and drone defence technology is always available.
A drone control system has to be built only for its specific drone model. In contrast, a drone defence system needs to cope with all drone types and their control systems available on the market. This is a challenge that can only be met with networked IoT security technology, from both a technical but also a financial point of view.
Cloud-based Security
Cloud Computing is the on-demand availability of computer system resources, especially data storage (cloud storage) and computing power, without direct active management by the user. The term is generally used to describe data centres available to many users over the Internet. Large clouds often have functions distributed over multiple locations from central servers.
Cloud-based Security describes the use of cloud computing for the purpose of providing security for people and property. Here, the cloud is the central element of the security system in conjunction with modern data network technology.
These security systems use corporate or private cloud systems, as opposed to a public cloud, which is accessible to essentially everyone. The technology of these two types of clouds is basically identical, the difference being only the level of the security measures implemented to protect these clouds. These security measures give only selected users and devices controlled access to the cloud, thus restricting flexibility.
Cloud computing is usually distributed over several redundant and secured data centres at different locations. A data centre in which a security cloud is hosted should be certified to comply with the following international security and Information Technology (IT) standards:
- Built and certified to Tier IVi standards;
- ISO 27001:2013 for highest information security;
- ISO 50001:2011 for comprehensive energy management;
- ISAE 3402 Type 2 Test Report;
- Payment Card Industry Data Security Standard (PCI DSS).
- Security Cloud applications are also characterized by:
- High-security encrypted data transmission;
- High-performance firewalls;
- Minimal latency through special routing concepts;
- Multicast capability;
- Designed to interface with various system technologies across sensors, effectors, as well as C2 centres;
- Support for all common data transfer protocols for data, text, audio, image and video;
- Fully scalable for data storage capacity and number of applications;
- Capability to separate, manage and monitor clients and missions.
All complex technical systems in the cloud are set up in such a way that their application in the field – including the required hardware – is as simple as possible and as secure as necessary: ‘plug and play’ and ‘easy to use’ also means minimal training effort on site. In addition, being networked with the cloud’s system support allows remote assistance for users on the job, if required, and keeps the entire system up to date.
Examples of Cloud-based Security Applications
Cloud-based Security for Consumers
For private use, a consumer subscribes to a service agreement with a private security company. The security company then provides the consumer with portable RF sensors. The consumer can now use these sensors at home, in his vehicle or anywhere else he desires. Via a small portable router, the RF sensor is then connected to the security company’s cloud over the cellular network. There, a user account is set up for the consumer and the secure connection with one or more RF sensors is established. Now the consumer installs an app on one or more mobile devices (‘cell phones’) and registers with this app on the security cloud. The application is now set up, and the consumer receives a warning whenever drones are near one of his active RF sensors.
Cloud-based Security for Government Agencies
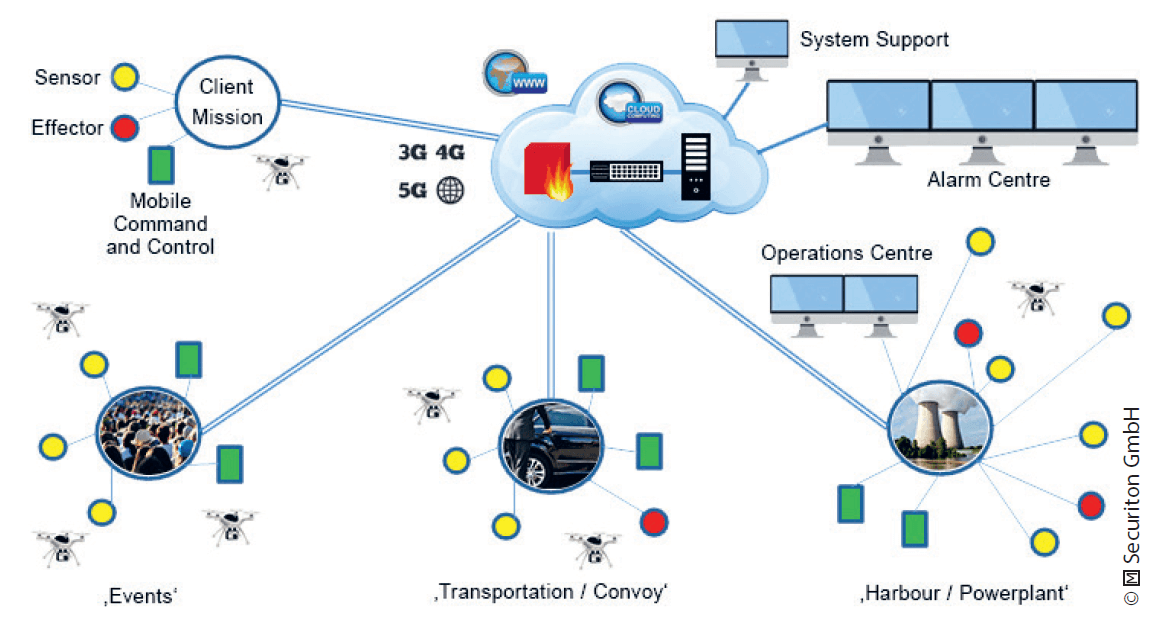
An application for governmental use is basically identical with the private use. A government agency such as the police or the military purchase the sensors and effectors for their officials to use and the security cloud is then set up and operated by the security agency. In contrast to the private user, officials may also have the authorization to use portable effectors to counter drone threats. Examples of such an operation would be large-scale incidents, such as accidents, natural disasters, or demonstrations, where unwanted private drones would interfere with the deployment of first responders and security forces.
Cloud-based Security for Mobile Applications
For large events such as music festivals, outdoor sporting events, street protests, military exercises or police operations, mobile counter-drone systems can be installed in trailers or mounted on vehicles and deployed to the area that needs to be protected. These systems may include a mobile C2 unit or the sensors and effectors can be connected to a remote alarm centre, both options utilizing the security cloud for event monitoring and response activation. When connected to the security cloud, security teams (with or without portable sensors and effectors) can be integrated into the system as well, so that they can swiftly respond to events wherever necessary.

Cloud-based Security for Stationary Applications
Critical infrastructure such as harbours, airports, industries, tourist attractions, stadiums, power plants, communication hubs as well as important structures of governments, militaries, or law enforcement agencies may have large and powerful sensors and effectors permanently installed and wired to the site’s power and data networks. If the infrastructure has its own operations or security centre, the sensors and effectors may be directly linked to it, so that the drone situational picture would be readily available to the security staff. Connected to a security cloud, the drone situational picture could be transmitted to other alarm centres such as dislocated security forces or the police who may then support with emergency response or other countermeasures.
Flexibility and Scalability of Cloud-based Security Applications
Cloud-based security is highly flexible and scalable. It can easily grow with the expanding requirements of the customer, be it an individual, commercial industry or a government agency. Sensors and effectors, mobile as well as static, can be integrated as needed, even if it is only temporary. Cloud-based security allows for swiftly adapting to a developing and dynamic drone threat by providing and distributing situational awareness where it is needed while supporting centralized as well as decentralized C2 of drone defence missions as required.
Cloud-based security also offers the possibility to share sensor data, countermeasures and security personnel amongst multiple co-located infrastructure. Large commercial or industrial areas with multiple businesses may collectively set up a drone defence system with a central guard force which protects all property in the respective area. The same approach may be feasible for governmental districts in capital cities or large logistic hubs where air, water, rail, or road transport lines merge.
Summary
Today, consumer and commercial drones are readily available to anyone and are becoming increasingly powerful, making them ideal instruments for criminals and terrorists to considerably expand their capabilities.
With cloud computing and IoT technologies, security systems for drone defence can be deployed quickly, easily, anywhere at reasonable cost. This permits drone defence applications to be maintained over a long period of time, with the necessary services, and at a level of performance that can keep pace with the rapid developments in drone technology.











