Introduction
It has been stated that Unmanned Aircraft Systems (UAS) are ‘re-shaping the cyber security world’.1 While this claim might seem overstated, there’s little doubt that the advancement and proliferation of UAS worldwide present many challenges to the cyber security community as UAS increase in sophistication and defenders scramble to keep up with the growing threat. However, while adversaries in possession of UAS exploit their capabilities and invent new avenues for attack, the UAS themselves are ‘highly exposed technical systems’2 and increasingly vulnerable to capabilities operating in and through cyberspace. Indeed, it has also been claimed that, in reference to countering UAS, ‘cyber or electronic attack on UAV [sic] may constitute one of the most direct and immediate ways of implementing cyber power’.3 A general understanding of the elements of Cyberspace is an important piece as it pertains to the multi-domain, whole of government approach to countering the UAS threat. The aim of this chapter is to provide an overview of Counter-UAS (C-UAS) concepts as it pertains to Cyberspace. This chapter outlines the Layers of Cyberspace, the Cyber Kill Chain, what is meant by ‘Counter’, Attack Surfaces, Vectors and Tools and includes a special note on the relevance of 5G technology.
UAS are ‘reshaping the cyber security world’.
Layers of Cyberspace
Familiarization with what constitutes the Cyberspace Domain is important to understand how capabilities can be brought to bear when C-UAS missions are being considered. At first glance, an UAS might be considered for the airborne platform itself (i.e. Unmanned Aircraft or UA) and only as a part of the Air Domain. However, taking into account the UAS in its entirety, and not the vehicle alone, it becomes clear that this first impression is over-simplified; the entire UAS consists of elements accessible through the Cyberspace Domain. The Cyberspace Domain can be described as comprising primarily three interconnected layers: a physical layer, a logical layer and a cyber-persona layer.4, 5, 6 The physical layer comprises the Information Technology (IT) hardware, the equipment and networking infrastructure for processing, storing and transmitting data. The logical layer includes inter-related but abstract elements such as data, operating systems, applications, network operations and protocols. The cyber-persona layer is a digital representation of an actor or identity created by the data and rules of the logical layer. A cyber-persona can be a person, multiple users, an alias, an entity or a machine. When considering C-UAS, all three layers should be assessed as possible attack surfaces.
Cyber Kill Chain
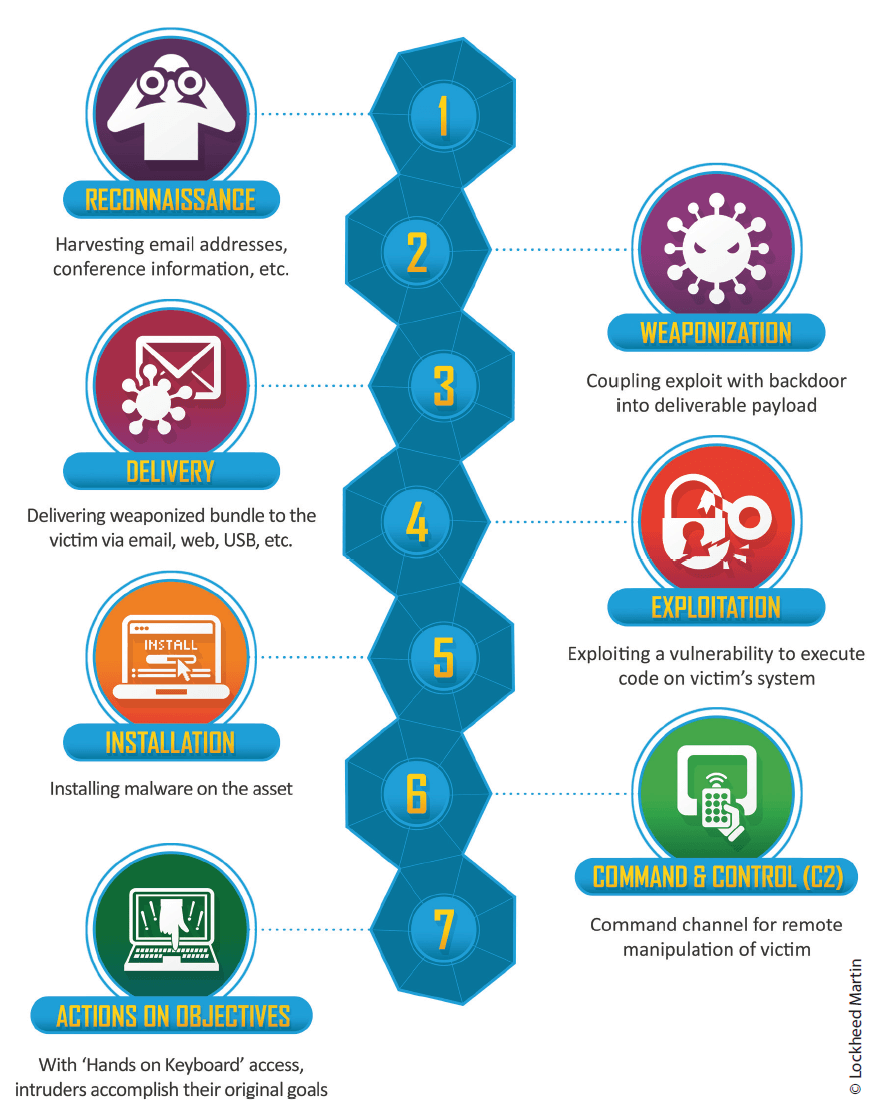
Generating effects in and through Cyberspace varies significantly in degree of difficulty depending on the target and desired effect, but the processes involved are similar. The progression from conceptualization through to achieving the desired effect is referred to as the Cyber Kill Chain and one of the industry’s more recognized modelsi was created by Lockheed Martin (LM).7 The steps in this process include Reconnaissance, Weaponization, Delivery, Exploitation, Installation, Command and Control and Actions on Objectives. Each phase presents unique challenges requiring varying degrees of sophistication and investment of time and resources, normally in direct correlation to the value (monetary or strategic) and the level of security afforded the target.
What Do We Mean by ‘Counter’?
C-UAS activities can be categorized into three distinct elements, ‘detection, non-interactive measures, and interdiction’.8 Detection activities employ a variety of sensors including ’acoustic, thermal, radar, visual or radio frequency (RF)’9 to identify the presence of a UA. Non-interactive measures are those employed in response to reduce the impact, such as warning and/or evacuating personnel from the area. Finally, interdiction refers to action taken to actively engage and influence a UAS. Therefore, C-UAS in this chapter is not referring to passive, defensive measures (technical and/or administrative) to protect our networks, data and critical IT infrastructure from attacks (i.e. firewalls, intrusion detection systems, antivirus applications, etc.) in order to preserve freedom of action. Rather, C-UAS in this chapter refers to active measures implemented to project capabilities in order to defend against UAS threats. Note that NATO, as a defensive Alliance, does not possess resources within either its command or force structure to conduct Offensive Cyberspace Operations, but its operational commanders are able to leverage sovereign cyber effects provided voluntarily by Allies, a process entitled SCEPVA10. How effects are generated in and through Cyberspace for C-UAS measures, and what transpires in each step in the Cyber Kill Chain, is ultimately determined by the objective, whether it is to capture, to exploitii or to destroy UAS components.
Capture
Capturing an airborne UA might well be considered the ultimate C-UAS response. Seizing an adversary’s high visibility asset not only eliminates it from their inventory and provides a source of intelligence about their capabilities, it can also have a significant impact on morale, improving morale of friendly entities and negatively impacting the morale of the antagonists. Capturing a UA may be achieved by spoofing GPS signals to direct the UA off course to an area where it can be retrieved by associates. One of two popular theories of how Iranian forces came into possession of a US RQ 170 Sentinel in 2001 was that the GPS satellite signal was ‘overlaid by a spoofed GPS-signal originating from a local transmitter with a stronger signal’11 which created a false indication of the UA’s position.iii Capture can also be achieved by intercepting the communications links in order to take control of the UA. With autonomous systems malware would have to be introduced before the flight to enter a new flight path and landing coordinates.12 It is possible to gain access (by keystroke loggingiv), and change authorizations or access permissions which will make it possible to alter permissions, privileges and authorization and take over and capture the UA. A keylogging virus was detected on US Predator and Reaper UASs at Creech Air Force Base in Nevada in September of 2003 ’logging pilots’ every keystroke as they remotely fly missions over Afghanistan and other War zones’.13
Exploitation
An adversary’s UAS might be exploited by leveraging its operation in order to help achieve one’s own mission goals, and ideally without the operator’s knowledge. UAS can be exploited through intercepting the sensor data, such as the video images to be able to view what an adversary is seeing and to analyze and interpret this for intelligence and force protection purposes. Another possibility is to ’compromise the keys and capture the communications’ (eavesdrop/passively monitor) or even ’modify or fabricate information’,14 in other words, intercept what an adversary is communicating and assess it for intelligence purposes (traffic analysis, forensics, location tracking) or change the content (identity Spoofing, Man-in-the-Middle attack, Message Forgery, Replay Attack) in order to deceive/mislead and influence their decision-making as part of an Information Operation or Deception campaign. Creating a Rogue Access Point would facilitate, depending on the Class and Type of System, accomplishing a Man-in-the-Middle attack, for example. Another, though highly sophisticated approach, would be to conduct a firmware replacement attack, the most opportune time in which to accomplish would be when a UAS is undergoing maintenance, particularly when software or firmware upgrades are taking place. Replacing the firmware with a malicious variant supports installing a back door to allow ongoing access to sessions with the UAS for continuous exploitation.15 Furthermore, having malware installed would permit influencing the performance, which, in turn, would enable increasing fuel depletion rates, decreasing the time of operation and reducing the length of a mission.16
Destruction
Destroying an enemy UA may be the most probable and more easily achieved C-UAS measure from the perspective of Cyberspace operations. Attacks to influence on-board sensors and alter data regarding (one or more of) location, altitude, speed, pitch, roll and heading etc., in order to cause the UA to either malfunction and crash, to self-destruct by flying outside its own flight envelope for maintaining structural integrity or to fly directly into the ground or another object and be destroyed are all plausible courses of action. Destructive attacks also have a better likelihood of avoiding detection or at least permitting plausible deniability considering that, historically, UA accident rates are 100 times greater than for manned aircraft.17
Attack Surfaces
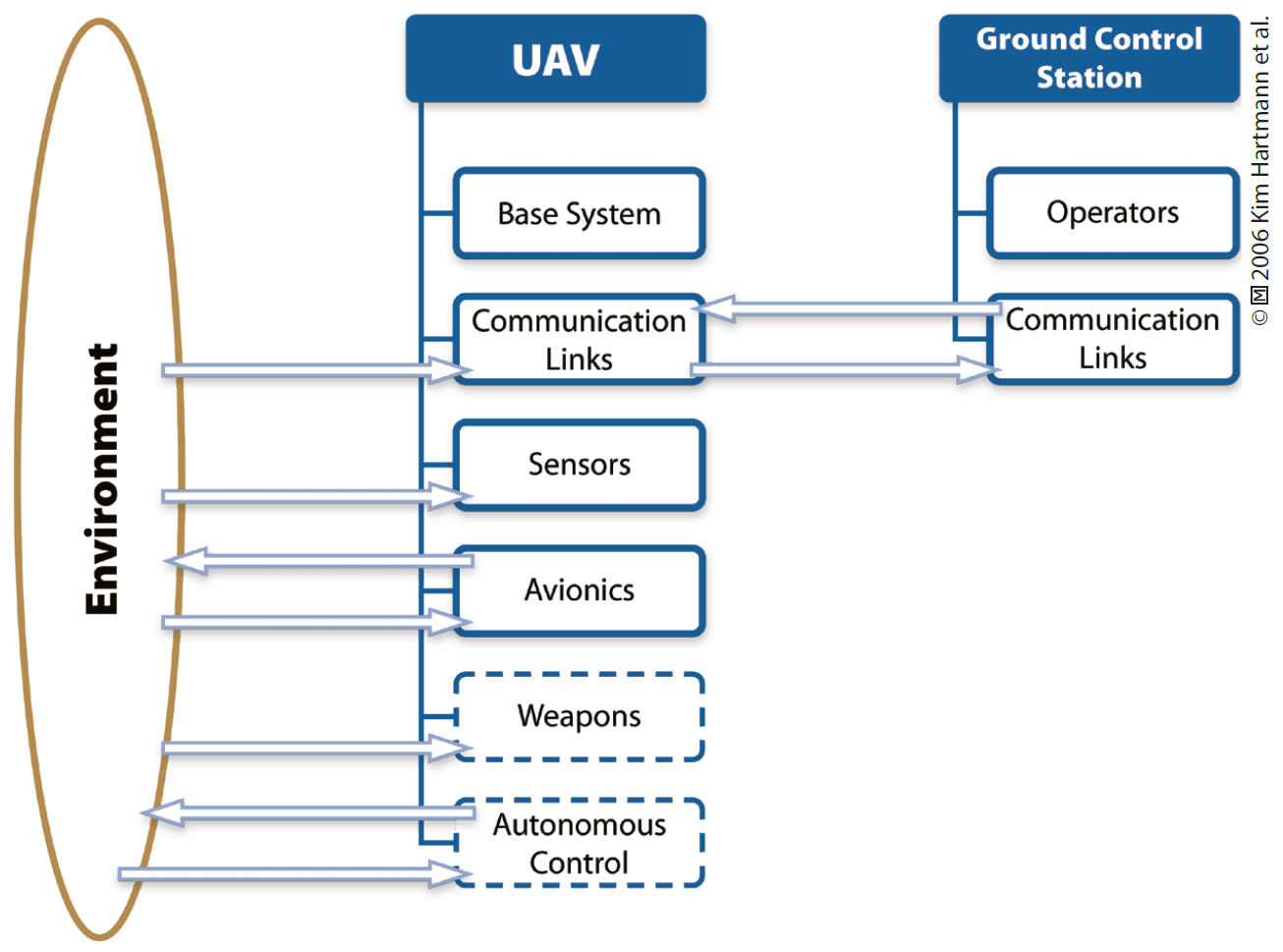
UAS vary a great deal in size and complexity. There is a wide array of UA according to their construction (e.g. the size, weight and payload), their operational capabilities in speed, range and endurance, and their electronic and mechanical design. Such differences result in a large field of UA with a wide variety of flight envelopes, degree of autonomy, level of sophistication and functionality. Regardless, whether small and designed for amateur use, or large and complex, designed for national defence purposes, all UAS are comprised of the same basic components (cf. Figure 11.2, p. 189) and are founded on similar principles. Additionally, the many types of UA should be considered as complex aerial vehicles and exceptionally sensor-driven assets.18
Most UAS operations require interaction in a three-dimensional environment under the continuous guidance of the operator and, therefore, require multiple on-board control sensors. Maintaining reliable and synchronized communication channels between these sensors assures the real-time data transfer and control of a UA. The main control elements consist of ‘physical infrastructure (external hardware), computer systems (internal hardware) and non-physical software’.19 Other principle elements common to UAS include the payload, operator, data links and support elements.
During flight, even when in autonomous mode (when applicable), several data links may be established forming a UAS network among one or more Ground Control Stations (GCS), ground-based antennas, Mobile Ground Units or many other UA (e.g. in the case of swarming). A communication link may consist of a continuous and dedicated data link connection, a partly-continuous and semi-dedicated connection, (such as Wi-Fi or Bluetooth), or ‘discrete connections’, based on pre-programmed flight plan uploaded to the UA through direct access to the hardware from external data storage devices, such as USBs and DVDs.20 Similar to any other IT network or operating system, UAS networks are crucially dependent on the information flow through the sensors, the links, the avionics and the hardware infrastructure.
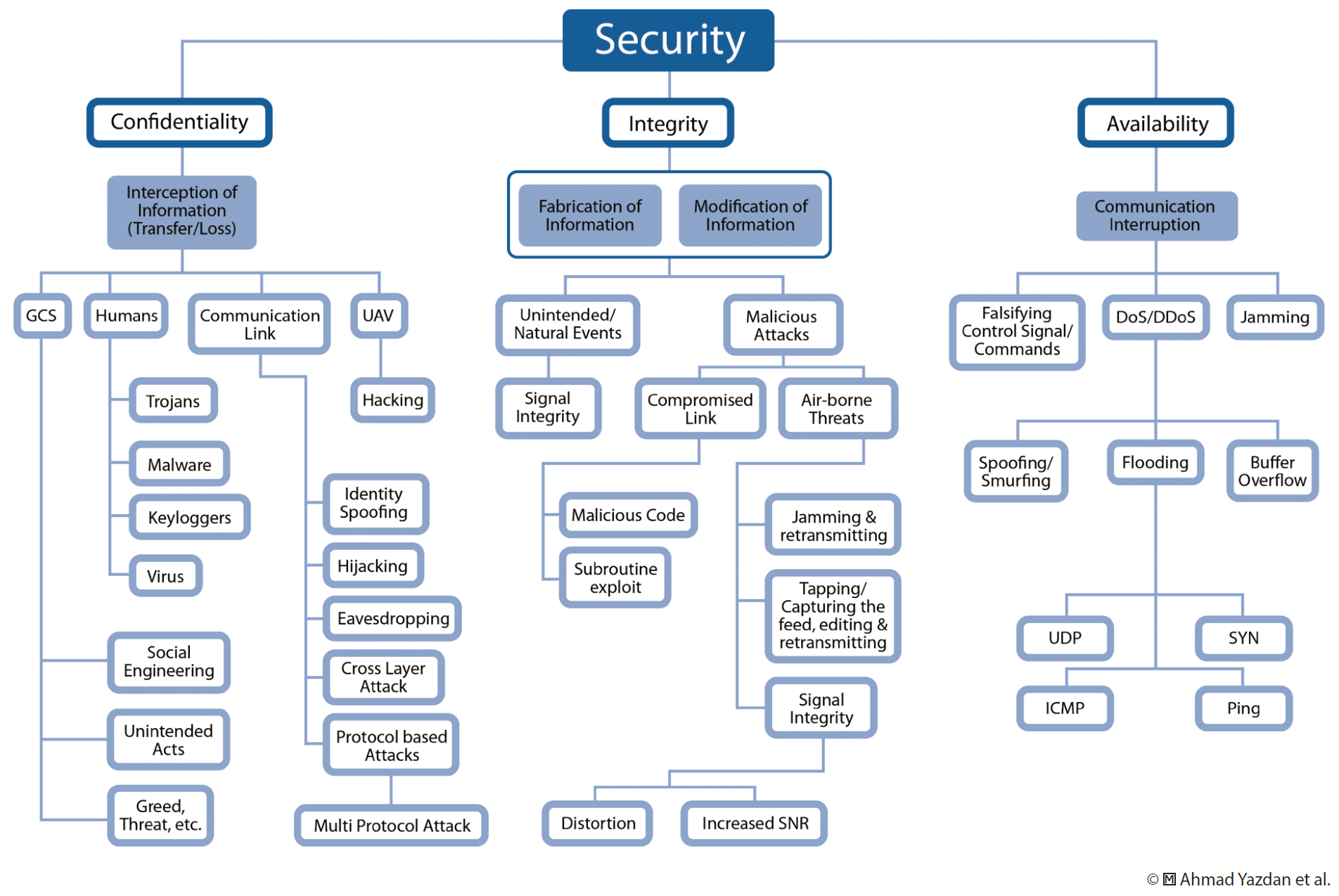
The more complex and sophisticated the system elements, the more attack surfaces and number of potential entry points to exploit. By implementing common attack vectors against these surfaces, such as backdoors in a network perimeter, software vulnerabilities, manipulating output data to actuators, compromising input data to controllers, Man-in-the-Middle attacks, database attacks and communications hijacking, it is possible to challenge the Confidentiality, Integrity, and Availability (CIA) of the data flow and, hence, interdict and influence the UAS.21 These forms of attacks are depicted diagrammatically in the ‘UAV System [sic] Cyber-Security Threat Model’ (cf. Figure 11.3). Remote Code Execution (RCE) is an effective countermeasure which targets not only the flying platform but also the UAS’s ground network system, exploiting security flaws and backdoors in firmware, weak passwords, unsecure protocols and software bugs.22 Moreover, the fact that many of the smaller commercial and consumer drones are using standard, commercially available smartphones as their control platforms, increases the likelihood of known vulnerabilities in the smartphone’s operating system to affect the UAS’ level of security.23
‘Cyber or electronic attack on UAVs [sic] may constitute one of the most direct and immediate ways of implementing cyber power.‘
Operators
The operators, whether human or automated, are subject to influence through Cyberspace. The scale of effects can range from trivial such as manipulating the conditions within the deployed climate-controlled shelters within which they operate, through to a sophisticated Information Warfare campaign that combines offensive cyber operations with online information operations that aims to influence how they operate and the decisions they make, to more extreme impacts such as contributing to conducting physical attacks on the operators. UAS operators in the Ukraine for example, suffered casualties after being located by Signals Intelligence and targeted by mortar fire.26 Operators can be targeted even when off-duty, such as via their e-mail or social media accounts, either to influence their behaviour and decision making or as a means to introduce malware into the UAS.
Communication Data Link
UA that are not autonomous are controlled in flight through a communications link referred to as the Common Data Link (CDL). Flight sensor and command data is transmitted via the CDL between the UA and the GCS. The CDL for UAS of short-range (and normally low altitude), such as Man-Portable and Tactical UAS, is via Line of Sight (LoS) that employs either an omnidirectional antenna or a directional antenna aimed at the GCS. Long-range UAS rely on Satellite Communications (SATCOM) networks for the Beyond Line of Sight (BLoS) links. The CDL for Military UAS employing SATCOM is likely encrypted and more difficult to attack.
UAS rely on ‘a nearly continuous stream of communications to complete the mission’.27 However, this CDL can be subjected to cyber-attack, principally with the purpose of gaining control of the
UA. Furthermore, because ’UAVs [sic] are highly dependent on external input and therefore provide multiple input channels’ they are difficult to harden.28 The CDL link can be tampered with, for example through a packet spoofing attack, whereby the attacker mimics the IP (Internet Protocol) address and MAC (Media Access Control) address of the controller since the UA will accept commands when the source IP and MAC addresses are accurate.29 In many instances if/when this link is lost, the UA will follow a process known as a Lost Link Procedure and first attempt to re-acquire the link, and, if unsuccessful, fly to a pre-programmed geographical position.30 C-UAS planning that involves interference with the CDL will take this feature of the onboard program into consideration, particularly if the objective is capturing the UA. Loss of the CDL occurs often, as a 2009 report cites that 15 percent of US Army UA accidents were caused by communications failures.31
Regarding frequencies, the Tactical CDL (TCDL) is a secure SATCOM link that normally operates in the Ku Band with an uplink in the 15.15 to 15.35 GHz range and a downlink at 14.40 to 14.85 GHz. The data has unique routing, encryption and multiplexing which makes it more difficult to attack. LoS link frequencies are often based on C-Band or Wi-Fi (IEEE 802.11 standard) b-/g- or n- standards with 4.4 to 4.94 GHz uplink and 5.25 to 5.85 GHz downlink. As Wi-Fi employs omnidirectional antennas for controlling UA, it is highly susceptible to eavesdropping.
Internet of Drones
UAS may also be employed to extend an adversary’s network connectivity in areas lacking critical IT infrastructure; this arrangement is referred to, in line with the term ‘Internet of Things’ (IoT), as the ‘Internet of Drones’ (IoD)32 In essence, the IoD refers to a configuration where many drones work together, simultaneously exchanging data, to form a network. They can be operated remotely via the Internet using IP addresses, and this feature opens the possibility for many new applications. At the same time, this means that these UAS are prone to the same security risks as all IP-based functionalities and are vulnerable to be influenced through Cyberspace.
Video Data Link
Apart from the CDL, many UAS employ radio links for additional operational features. Full Motion Video (FMV) is relayed to a Remote Viewing Terminal via a Video Data Link (VDL). This link is also a potential target for exploitation where the link can be intercepted and the images assessed for intelligence by agents other than the operator. In the summer of 2009 US forces discovered days’-worth of US UAS video footage on Iraqi insurgents’ laptops which the insurgents were able to capture with software worth $26 (USD)33 Furthermore, there is evidence of another instance where Israeli UAS video imagery had been intercepted by British forces.34
Base System
A UAS is, at its most abstract, an information processing system. Data is sensed, processed, shared, and communicated in order to control flight parameters (speed, altitude, etc.).35 as well as to collaborate with other UAS within a complex networked environment. UA ‘are essentially flying – and sometimes armed – computers’36 and the base system can be considered the operating system. Therefore, the base system is vulnerable to cyber-attacks comparatively to other information processing and operating systems. Since the Base System is central to the UAS, linking the components, controlling the sensors, navigation, avionics and communications and integrating other optional components such as special sensors and weapon systems, it is considered a key target for a cyber-attack.37 With UA being highly technical and prone to faults, many contain Fault Handling Mechanisms (FHM). These FHM could be considered as attack vectors as well, where common functions such as ‘self-destruct, automatic-return, land and hover’38 might be exploited, depending on the desired effect.
Sensors
The UA’s sensors include the sensory equipment and integrated pre-processing functions and can be classified according to whether the references are external or internal.39 Inertial Navigation Systems (INS) are internal sensors, as they detect internal physical parameters such as acceleration or angular rates. Cameras, GPS and Radar are external sensors as they receive information from the environment. Sensors with external references are more susceptible to spoofing and false signals. Internal sensors can drift and deviate from the correct value particularly without synchronization with external sensors so there are inherent errors, but they are less susceptible to attack through the sensors.40 UA can be outfitted with a variety of different sensors. These include but are not limited to Electro-Optical (EO) and Infra-Red (IR) cameras, low altitude altimeter, Laser Range Finder Designator (LRFD), Synthetic Aperture Radar and Ground Moving Target Indicator sensor (SAR/GMTI). Each sensor provides another attack surface, another vector to engage the UA. The sensor system should be viewed as ’a continuously open input channel and may hence be prone to attacks’.41 Directions on how to spoof the GPS signal on civilian and military GPS receivers as well as to covertly take over the satellite-lock (a connection synchronised in time and frequency) are posted online for all to see. The possibility of spoofing sensors becomes less likely where data is cross-checked, mutually-enhanced and automatically fused to create a single optical image, as is the case with the MQ-9 ‘Reaper’ UAS which combines infrared, daylight and light enhancing camera imagery, via the Multi-spectral Targeting System (MTS-B).42
Avionics
The avionics system converts the signals either received on the communications channel or pre-programmed (autonomous) to adjust the engine and control surfaces (flaps, rudder, stabilisers, spoilers, digital accelerometers, geofencing software). ’All of these offer a means by which safe operation can be compromised’.43 UA can be impacted by cyber-attack (such as gain scheduling or fuzzing attack) the effects of which can result in deviations from the values of the altitude, speed, heading, bank angle and/or the pitch angle.44 Many well-known drone manufacturers, e.g. DJI, for legislation reasons, have embedded geofencing software in their products to prevent them flying over security-sensitive areas, such as airports. However, this still voluntary practice cannot be applied effectively for all areas and by every system.
Weapons Systems
Information regarding capabilities to conduct cyber-attacks against Weapon Systems is classified and beyond the scope of this publication. That said, the Weapon Support Systems component of specific UA enable them to carry, launch and operate weapons. It may be enough for C-UAS operations to influence the UA, as controlling the UA may provide sufficient control of the weapons system to meet mission requirements.
UA ‘are essential flying – and sometimes armed – computers’.
Data Storage
Many UAS can store up to 30 days of continuous ISR data. However, since the UA sensors can be influenced, whether the stored data is targeted may be less of a factor. Further, the suspected value of the data that is collected and stored will influence the decision what countermeasure to attempt. If the data is desired with no concern whether the adversary is aware, then attempts might be used to capture the UA. If the intent is to acquire the data without the adversary’s knowledge, for intelligence or to deceive, then the efforts will be dedicated to exploiting the UAS and copy or alter the data without the operators’ knowledge. If, however, the objective is only to keep the data from the adversary then the UA could be destroyed or the data deleted. The storage state will influence the course of action. For example, volatile storage such as RAM (Random Access Memory) is more accessible to compromise of confidentiality. Encryption of the data will protect the confidentiality, but it does not prevent it from being overwritten or being deleted.45
C-UAS Cyber Vectors and Tools
Overall, GPS spoofing and Denial of Service (DoS) attacks are the most common C-UAS attacks, and hijacking and destroying UA are the most common results.46 Passwords are a top priority target in order to gain control of UA and this can be accomplished by tools that execute dictionary attacks, brute force attacks or statistical attacks. Man-in-the-Middle attacks are conducted to exploit UAS and these can be accomplished by eavesdropping and URL (Uniform Resource Locator) manipulation. DoS attacks are used to deny the service to UAS operators and this could be achieved by draining system resources such as processing cycles, power or memory by continuously flooding the communications with requests.47 Tools are available to sniff UAS Wi-Fi connections, conduct packet capture and export data as text files, create fake access points, deauthenticate legitimate operators, upload malware (e.g. Maldrone – malware for drones), and execute Buffer Overflow or Cache Poison attacks.48 These represent but a few of the many possible types of cyber-attacks against UAS.49 A synopsis of all the cyber-attack vectors and all common tools is beyond the scope of this chapter. Overviews of many common cyber-attack vectors have been published50 and more tools will continue to be created. In fact, technologies continue to be developed to enable cyber-attacks against UAS (SkyJack, Maldrone, Aircrack-ng and others) and techniques (narratives and videos) on how this can be accomplished are posted online for anyone to access.51 While applications are available to the public which enable C-UAS in/through Cyberspace for commercial drones, C-UAS capabilities for use against hardened military UAS are classified state secrets and the ability to create and properly Command and Control such effects to reduce unpredictable events remains a ‘high art’ of which only a few nations are capable.52
‘The ability to create and properly Command and Control such effects to reduce unpredictable events remains a “high art” of which only a few nations are capable.’
A Special Note on 5G
With the advent of 5G, the next generation of wireless and mobile network, the global commercial and consumer drone industry is likely to change drastically. Although strictly regulatory, frameworks are already in place to restrict commercial drones from flying in restricted airspaces. The fact that the 5G infrastructure, especially in urban environments, ensures uninterrupted wireless connection to the Internet, extends the range of small UA beyond the LoS of the controller.
5G’s new network architecture allows data rates of up to, theoretically, 10 Gbits/sec, enabling real-time transmission of data and video. Also, this speed reduces the latency to less than 1 ms and ensures the devices will stay connected regardless of their velocity. Finally, 5G exponentially increases the capacity for interconnectivity allowing thousands more IP devices and users to be connected in a small geographical area (network cell).
5G is going to become an absolute game-changer for small- to medium-sized UA as it will provide them not only greater scalability than with 3- and 4G, but also the possibility of BLoS flight, and ubiquitous coverage. For instance, swarming technology is likely to evolve further and military operations will include increasingly more deployable drones with operational squadrons of manned aircraft. Regardless whether small UAS swarms will ‘operate as a single body to perform a single function (cooperative swarming) or they perform separate distinct tasks in coordination with each other (coordinated swarming)’,54 it will be possible to control swarms by a single operator and in real-time as a result of 5G networks.
To date, C-UAS methods and products have been focused on addressing single UAS threats. As a result, swarming technology enhanced by 5G and Artificial Intelligence (AI) may seem invincible in the immediate future. Exploiting adversaries’ UAS swarms can only be achieved by expanding upon the same technology, tools and methods. Sophisticated sensors, tracking software, multi-faceted and mixed detection systems, and advanced AI algorithms will be required for an effective C-UAS.
Conclusion
Carter has written that ‘The threat of UAS is the strongest multi-domain battlefield weapon of our time’.55 While such a claim may seem extreme, it remains that effects produced in and through Cyberspace are considered one of the preferred avenues for C-UAS efforts. Being able to bring to bear the capabilities described in this chapter requires a great deal of sophistication and investment of time and resources. Solutions involving Cyberspace are undoubtedly an objective of those nations developing C-UAS programmes and have the ability to project capabilities in and through Cyberspace. Comprehensive knowledge of the targets is critical and here too, the Cyberspace Domain would figure prominently. Cyber espionage activities will be at the forefront of gathering intelligence into Research and Development, Design, Manufacturing, Logistics and Supply Chain processes as part of the Reconnaissance, Weaponization and Delivery stages of the Cyber Kill Chain. However, Cyberspace capabilities are only one element in what should be a broad approach to C-UAS. In short, ‘one vector of C-UAS will not solve an issue, other disruptive technologies will have to be combined’ to provide a comprehensive solution to counter the UAS threat, as described in the other chapters in this publication.56
‘One vector of C-UAS will not solve an issue, other disruptive technologies will have to be combined to counter the UAS threat.’
Acknowledgements
Special thanks to the following people for providing clarification and recommendations during the drafting of this document:
Carolyn Swinney, RAF | Paul Withers, RAF | Hervé Lahille, EAG | Laura Brent, NATO HQ | Nikolaos Fougias, CyOC | Alan Sewell, NCIA
Glossary
- ARP Poisoning Attack: Sending malicious Address Resolution Protocol (ARP) packets to a network gateway table and altering the IP (Internet Protocol) and MAC (Media Access Control) address pairs in order to redirect the target’s data to a different system.
- Backdoor: A method by which users (authorized and unauthorized) are able to by-pass normal security measures and gain access to a system. Backdoors may have a legitimate use and pre-exist to enable System Administrators access. They may be used for nefarious purposes, even created, to allow malicious actors continuous, covert access to a system.
- Brute Force Password Attack: A method of cracking a password by systematically attempting different passwords with the intent of eventually guessing the correct password.
- Buffer Overflow Attack: An attacker fills a block of memory (buffer) with more data than there is space allocated in order to force the system to execute arbitrary code to take control of the system or cause it to crash.
- Cache Poison Attack: Replacing legitimately saved data in a temporary storage area (cache) with corrupted data that contains malicious code such that when the compromised data is sent to, or called up by, the client the malicious code will infect the target with malware.
- Cinderella (Time Provision) Attack: Malicious activity aimed at changing the target’s clock so that the system’s security applications licenses expire and renders the target system vulnerable to exploitation.
- De-authentication: Targets the communication between the user and a Wi-Fi access point by sending disassociated packets and effectively disconnecting the devices.
- Dictionary Password Attack: A method of cracking a password by attempting combinations including common words in the dictionary, numbers and symbols or previously used passwords from lists acquired from security breaches.
- Distributed and Denial of Service (DDoS, DoS) Attack: A DoS attack is when an attacker seeks to make a system unavailable for its intended purpose typically by flooding the targeted system with more requests than it can process which overloads the system and causes interruption of service. These attacks are relatively simple to conduct, even by unskilled attackers. If the source of the attack originates from multiple, coordinated infected hosts it is referred to as a DDoS attack.
- Eavesdropping: A type of man-in-the-middle attack where the attacker makes an independent connection with a victim and relays messages such that the victim believes he/she is communicating with a legitimate party.
- Elevation of Privilege: The attacker gains elevated rights to a network, its data and applications due to programming errors or design flaws and is then able to perform unauthorized activity.
- Firmware Replacement Attack: Altering the instructions stored in the flash ROM (Read Only Memory) of a device for malicious purposes. The instructions on firmware can be altered in legitimate cases to allow the devices to work more efficiently or function with new operating systems or devices; this occasion can provide the opportunity to covertly modify the instruction set.
- Fuzzing: A software testing technique of finding exploitable vulnerabilities by randomly entering different permutations of data (invalid, unexpected or random) into a program to promote abnormal behaviour.
- Gain Scheduling Attack: Influencing the attenuation of non-linear dynamics by attacking the systems that use a family of controllers, each of which provides control for different operating points in a system. For example, in aircraft flight control, the altitude and speed might be scheduling variables.
- Keystroke Logging: Recording the keystrokes on a keyboard, normally without the user’s knowledge, to capture the instructions and data exchanged between the controller/operator and the UAV.
- Maldrone: A malware installed and executed in a drone’s firmware in order to impact its performance for purposes other than originally designed or perhaps expected by the operator.
- Man-in-the-Middle (MitM) Attack: Covertly relaying, and possibly altering, communications between two or more points such that the parties believe they are communicating with each other.
- Masquerade Application: When malware is embedded in a legitimate application or when malware is disguised as a legitimate application but executes functions unknown to, and unauthorized by, the user.
- Packet Spoofing: Executed by mimicking the IP Address ad MAC address of the legitimate controller, the drone accepts the commands of the rogue agent.
- Port Exploitation: Using Internet-connected communications ports required for specific functions for malicious purposes, normally undetected by the operators. This can facilitate service disruption or data theft among other activities.
- Protocol Vulnerability Attacks: A general term to describe malicious and/or unauthorized activity against systems by exploiting weaknesses in the rules (protocols) that define how two or more components within a communications system connect and exchange data.
- Replay Attack: Delaying the transmission of valid data and re-transmitting altered data in its place without the need of decrypting the message after capturing.
- Rootkit Attack: The attacker installs malware on a computer in order to maintain privileged access to areas of its software normally restricted to a limited number of authorized personnel.
- Secure Socket Layer (SSL) Interception Proxy: The process of intercepting encrypted internet communication between the client and server without the consent of both entities.
- Statistical Method Password Attack: A method of using mathematical statistics to determine passwords with a higher probability of being correctly guessed.
- Traffic Analysis: The process of intercepting and examining communications to gain information on transmission patterns. Traffic analysis can be accomplished even if messages are encrypted.
- URL Manipulation: Altering the parameters in the Uniform Resource Locator (URL) such that a web server will deliver information to those without authorization.