Introduction
In general terms, Research, Development and Acquisition (RD&A) can be loosely defined as the efforts undertaken by companies and governments to innovate and introduce new products to achieve or enhance specific capabilities. Therein Research and Development (R&D) can be understood as the process towards the maturing of technologies, while acquisition is widely recognized as the bureaucratic management of the procurement process that deals with the investment in technologies, programs and products.1
Commonly, RD&A is separate from most operational activities not expecting immediate benefit but aiming for long-term advantages of the sponsoring entity. That accounts even more for defence-related RD&A, which are typically not constrained by classical market rules mainly due to the much greater complexity of the user and a general absence of a profit motive by governmental agencies.2
While the definition of necessary capability requirements is an inherent part of acquisition processes, R&D cycles are less the subject of outside demands than of focused investments and time. The following chapter shall show basic observations and trends of RD&A in the past, highlighting findings specific to C-UAS RD&A. Moreover, it will outline acquisition and cost-related aspects important for C-UAS technologies and finally drawing conclusions specific to the future development of such systems.
Technology Development
To grasp the complexity of RD&A, it is necessary to understand the individual maturity stages, their integration and transfer towards products as well as the targeted market. Neither Research nor the Development of individual Technologies or Systems is a linear process of which the timelines or end states can be accurately predicted.
One prominent example can be found in Graphenei and related applications. After its first discovery in the early 2000s, it was quickly attributed with a game-changing nature. Despite Graphene’s superior properties such as electrical and thermal conductivity, barrier properties and high strength, the research struggled to utilize it in a larger scale. This is mainly due to the fact that it is not trivial to upscale Graphene technologies in an affordable way.
Hence, the initial ‘hype’ was followed by smaller steps than expected leading to partial disillusion.
Assessing the Maturity of Technologies
The concept of Technology Readiness Level (TRL) is well understood and commonly used by the scientific community to describe the maturity of technologies ranging from the observation of basic principles (TRL 1) to the prototype demonstration in a relevant environment (TRL 6) towards ‘mission-proven’ systems (TRL 9). Originally introduced by the National Aeronautics and Space Administration (NASA) in the late 1980s, the nomenclature is also used to evaluate specific research projects or individual technologies.
While the taxonomy of TRL is best suited for individual technologies, it lacks the structure to assess the maturity of complex systems comprising multiple emerging technologies. Instead, other methodologies such as the System Readiness Level (SRL) are used to provide a qualitative and quantitative estimate of the level of readiness of a system. Those models, based on matrix algebra approaches, are the attempts of individual organizations to quantify and mitigate risks related to technology developments. In contrast to TRL other Readiness Levels are relatively new and not that commonly used.3
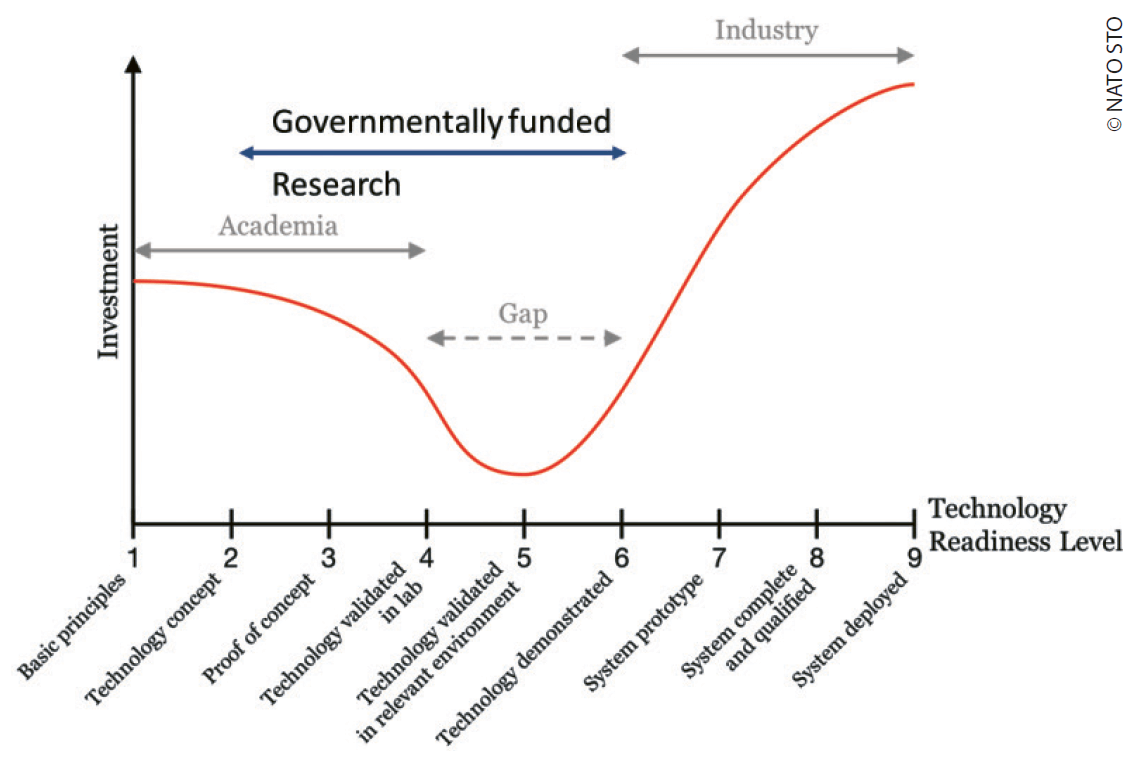
Even if technologies mature, successful transition to neither applications nor capabilities is certain. A phenomenon known as Valley of Death symbolizes the challenges for academia, governmental research and industry to operationalize ideas. While precise definitions vary, the principle problems can be summarized as the lack of funding, the cultural differences between academia and industry, the absence of customer awareness or an ever-changing requirement space.5 Governmentally funded research institutions such as the German Aerospace Center (DLR) are designed and tasked to carry out the necessary Technology Transfer towards a real-life product in close cooperation with academia and industry.
From Technology to Capability
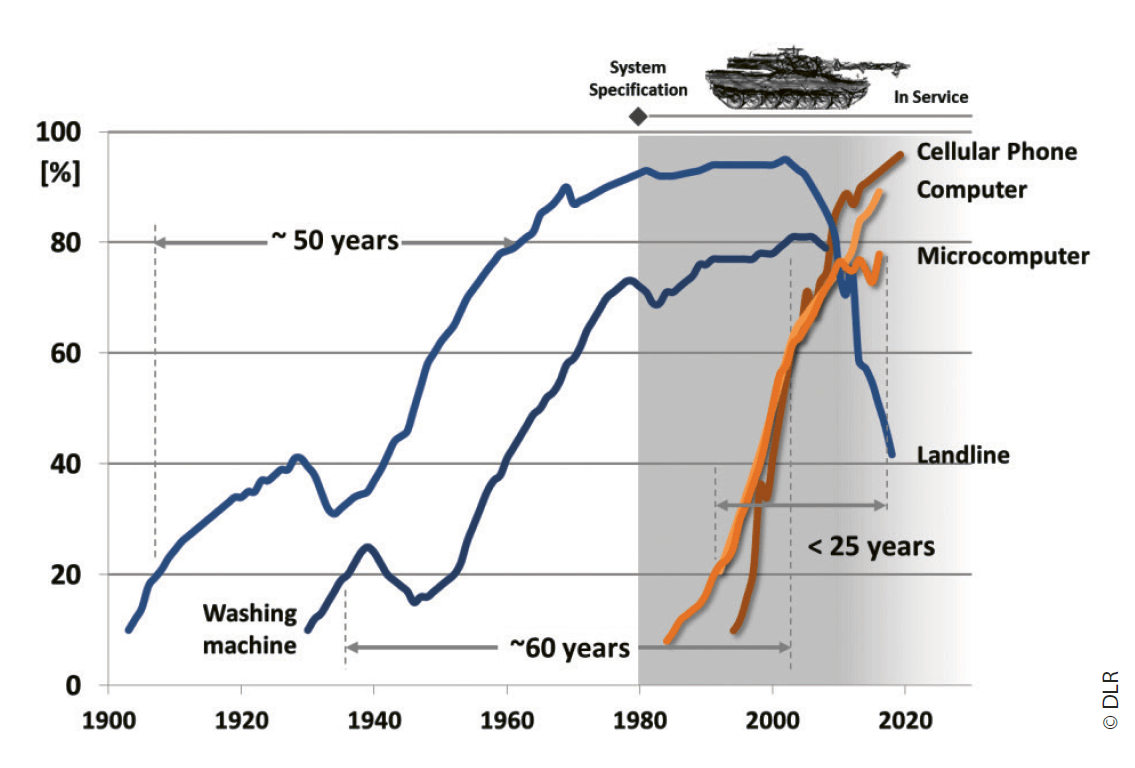
To be successful, an emerging technology or a novel system will not only need to be mature, rather it requires a broad understanding and adoption by the user. If not forced, that is more a function of time and costs rather than the technology itself. Today’s widely used technologies such as landlines or washing machines needed more than 50 years from entry to the market to full market penetration.6
In other words, technological driven military disruptions often need decades to mature and to be operationally effective. That can anecdotally be illustrated by the 36 years necessary from the Baldwin Patent for an internal combustion engine in 1879 to the first tanks entering the military inventories in 1915 resulting in Mechanized Armour; or the appearance of first operational Jet Aircraft, the German Messerschmitt 262, on the battlefield in 1944 rooting back to the 1910s Coandă Ducted Fan.
In the last forty years, the adoption of new products by the market has accelerated as has the pace of technology developments in specific fields. Moore’s Law is one of the most illustrative examples based on the observation that the number of transistors in a dense integrated circuit doubles about every two years. Microprocessors being the basic technology for numerous applications, their exponential growth in performance leads to numerous of other new technologies. Unlike common market mechanisms, military acquisition programs had struggled to adapt at the same pace.7
To be truly relevant for or successfully utilized by the military, RD&A has to be closely aligned with doctrinal and conceptual developments. The current Chairman of NATO’s Military Committee, Air Chief Marshall Sir Stuart Peach, argued for the necessity of the militaries to define ‘[…] the relevant military use […] rather than technology telling people what they can do, […]’.8
Specifics to C-UAS Technologies
As it is possible to draw general conclusions for RD&A, it is also possible to have a closer look into specific key technologies relevant to countering Unmanned Aircraft Systems (UAS). Aside from the specific technologies, we must also include the UAS and C-UAS ecosystem to understand the dynamic that is characteristic for this market and has to be considered for any RD&A decisions.
Since the acceleration of the United States’ global UAS operations in the beginning of 2008, the numbers and types of UAS have rapidly evolved.9 While the military user was the major driving force behind the utilization of UAS in the very beginning, the rise of commercial manufacturers and the introduction of new business models have shifted that situation. A broader technological basis and decreased costs have allowed a wider utilization of the required technologies allowing defence related RD&A to focus on add-on research.
Maturity of Counter-UAS – Reality Check
A first indication of the current maturity and expected advancement of related technologies can be derived from strategic technology assessments such as the Gartner Hype Cycle model. It characterizes the exemplary progression of emerging technologies from an enthusiastic innovation trigger through a period of disillusionment to an understanding of the technologies utilization.10 Although not fully congruent for some technologies, those general trends give a good understanding and comparison over time.11
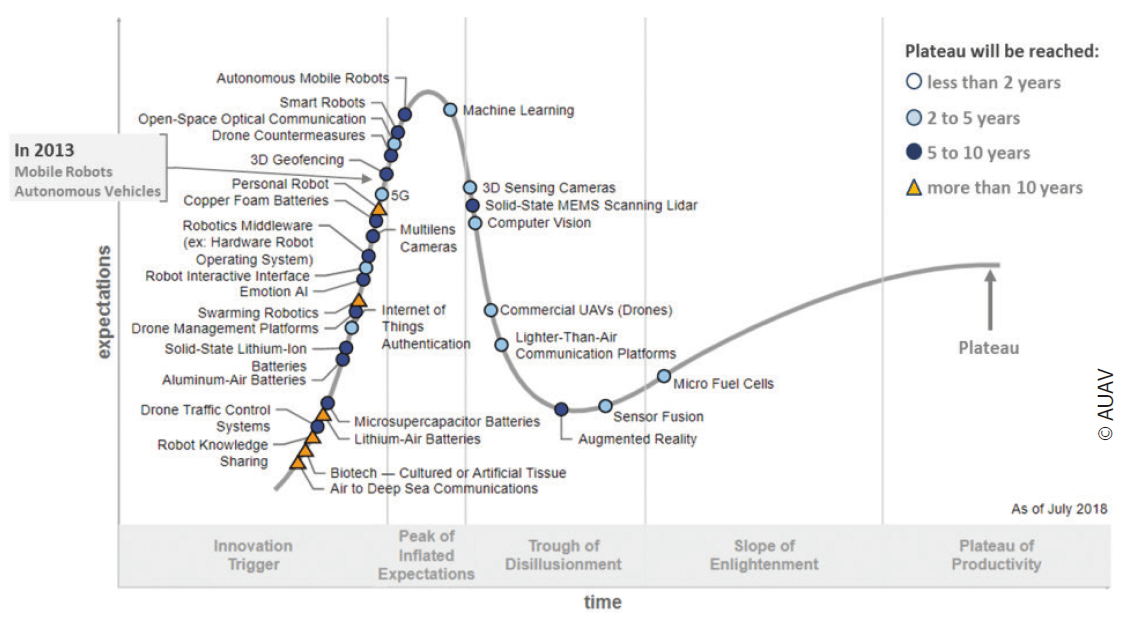
According to Gartner, Mobile Robots and Autonomous Vehicles reached their peak of expectations for civil applications in 2013. Half a decade later, technical and non-technical obstacles remain preventing them from utilization for day-to-day operations such as integration in the civil airspace or performing long-haul flights, especially for small UAS and drones. Nevertheless, a steadily growing number of market entries beyond private customers indicates growing maturity.13
Highly Dynamic Interaction Between Market and RD&A
Following a similar pattern, exemplary C-UAS technologies such as 3D Geofencing or general Drone Countermeasures are experiencing their medial overenthusiasm while others have already claimed to be operational ready reaching their plateau in the near future.14 Taking into account that successful C-UAS operations require the interplay of the whole processing chain stages, maturing only isolated stages will make them not operationally effective.15 For the very reason that the advancement of commercial and military Unmanned Aircraft will result in more performant systems, numerous research questions around technology, safety, practicality, policy, and legality of C-UAS measures continue to be of high importance.16
Meanwhile, the market of C-UAS systems and the number of manufacturers have skyrocketed. As of September 2019, at least ninety-five countries operate UAS and the number of market available C-UAS systems or sub-systems has exponentially increased from about 12 in 2015 to 537 in 2019. At the same time, the number of manufacturers increased to about 277.17 Furthermore, a steadily growing number of tier suppliers at all levels has resulted in multi-level partnerships accelerating innovation for both Unmanned Aircraft and Counter Systems, in hardware, software and services.18
Multifaceted and Multi-layered Threat – No Single Solution
The current non-technological as well as technological landscapes including industrial solutions do already indicate the fast amount of future challenges posed to C-UAS Systems. Given the multifaceted and multi-layered threat environment, the response cannot be based on single solutions in any of the processing chain stages or for any given military scenario.19
‘[…] it has proven difficult to identify and mitigate threats using currently fielded technologies’,20 which is mainly due to drawbacks such as camera systems being degraded by weather conditions, radar systems picking out low flying small UAS and drones very late or interdiction methods only working for specific entry modes.21 However, the aforementioned dynamics in R&D and market demand indicate that the rapid advancement of individual technologies will be very likely, but the effectiveness of counter-measures will still rely on the ‘weakest’ stage in the process chain. Hence, even if all individual elements of C-UAS or air defence capabilities are well developed and in place recent developments in UAS operations in Libya show that the effectiveness of C-UAS can be limited if confronted with an overwhelming number of UAS.22
Challenges for Technology Research – the Cat and Mouse Game
‘This threat is evolving every three to six months – it is just that adaptive … This is going to be a continuing challenge due to the adaptive nature of the problem of being able to use small drones in so many different ways and you cannot rely on one technique to respond to them.’ 23
Vayl S. Oxford, Director, US Defense Threat Reduction Agency, March 2019
In the absence of fully autonomous capabilities operating drones still relies on the smooth interplay of all Unmanned Aircraft System Components as introduced in Chapter 1 (cf. p. 13 f.). The complexity of comprehensive C-UAS operations has been introduced in Chapter 4 (cf. p. 55 ff.), show-casing numerous possible entry modes to disrupt that interplay of technologies.
Since militaries are generally depending on most of those technologies, not only for UAS operations, significant efforts and resources are devoted to ensuring their smooth operations also in contested environments. A kind of an arms race has already started either intentionally by the defence and security sector or unintentionally by manufacturers improving their products. Some of those efforts can be already found in the available literature and current research portfolios of nations.24
Robust Navigation – Current Effectors Might Fail
To navigate a UAS and drones properly, accurate values of its position and orientation are needed. Therefore, usually data from a space-borne navigation system like the Global Positioning System (GPS) are used. The signals coming from such systems can be jammed or spoofed, causing the loss of the system or at least a mission failure. Besides, GPS signals are degraded or absent in many areas hampering the operational use of UAS.25
The majority of market available effectors of C-UAS systems use these two aforementioned countermeasures. Hence, great efforts are currently underway by militaries but also civil UAS and drone manufacturers to harden their products towards more resilient modes of navigation.26 Countermeasures dealing with this problem are described in the following paragraphs.
Jammers can be countered by using a Controlled Radiation Pattern Antenna (CRPA), which either can steer the radiation pattern of the array to form a spatial null towards the jammer or to provide additional gain towards the satellites. A notch filter in the receiver frontend can mitigate Continuous Wave (CW) signals, adaptive notch filters can be used to counter chirp signalsii to a certain extent.
In this context, it has to be mentioned that low-cost Commercial off-the-Shelf (COTS) receivers are often more robust against chirp jammers than professional receivers. COTS receivers often have very narrow front-end filters, so that the most part of the chirp ramp is suppressed by these filters. Professional receivers usually use front-ends with a broader bandwidth. This allows a more accurate measurement but also increases their vulnerability to chirp jammers. To fill this gap, wideband Global Navigation Satellite System (GNSS) signals like Galileo E5 or Galileo PRS allow advanced mitigation techniques.
To counter Spoofing, the use of array antennas is a feasible method. So the footprint of the signal can be as small as possible, and a side interaction suppressed. More actively, arrays can be used to assess the directions of incoming signals indicating whether the signal is artificially created or from different satellites. Also, internal information generated by a UA’s or drone’s inherent sensors can be used to identify a spoofing attempt and to react. Meaconingiii can be countered by the same techniques used to navigate in GNSS denied environments.
On-board Navigation and Positioning – Hampering External Manipulation
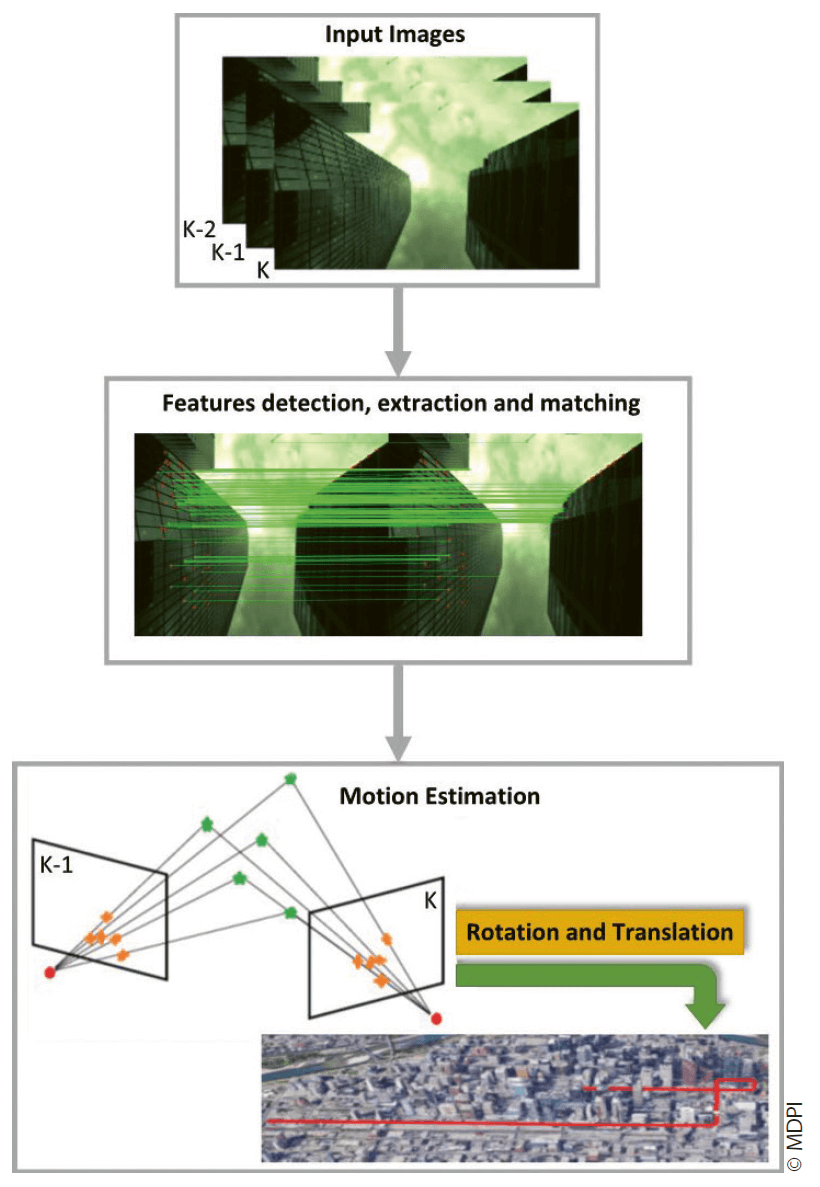
In the absence of external navigation information, an onboard initial measurement unit has to provide the required data. A localisation and mapping algorithm can build up a live map which, in combination with a visual sensor, can be matched to the currently captured image of that sensor. Another possibility is Visual Odometry (VO), a procedure which estimates the position and orientation of the UA analysing the deviation induced by the motion of the vehicle regarding images captured by onboard visual sensors (cf. Figure 24.4, p. 447).
Future techniques will use not only visual cameras but also information coming from microwave sensors like radar images. In combination with information generation based on Artificial Intelligence (AI) algorithms, the position and orientation of the UA can be calculated more accurately. New technologies with respect to quantum navigation and timing can also lead to accurate, independent positioning and navigation of UAS.28
New Command and Control links – Expanding UAS Performance
Safe operation of UAS requires a stable command and control link between the pilot on the ground and the UA. Conventional links will gradually deteriorate when the distance increases, making the link more vulnerable to interference and sudden condition changes, which in turn can compromise safe flying. New network technologies offer promising solutions. An example is the usage of Internet Protocol (IP) datalinks based on commercial Long-Term Evolution (LTE) networks or specific Information Technology (IT) infrastructure. Multi-static transmitters, robust coding schemes as well as the very high sensitivity of receivers offer unique conditions for robust communication to small UAS and drone swarms.29
UAS carrying a variety of sensors for monitoring and surveillance generate new needs for large data transfer in real-time. Free Space Optics (FSO) communication provides data rate capabilities of up to several Gbit/s at unprecedented distances with low transmitter power and therefore is superior to all possible microwave and Radio Frequency (RF) solutions. FSO allows for very narrow and directional beams, is immune against electromagnetic interference, and cannot be detected with RF meters or spectrum analyzers. It is the ideal technology for robust, secure air-to-air and air-to-satellite data links.30
Distance and Speed – Shrinking the Response Window
Slow-moving and non-stealthy UAS are easily targeted by state-of-the-art C-UAS. However, the effective detection range, especially for low, slow and small (LSS) UAS, can be only a few hundred meters or less given the terrain characteristics and height. Even with high detection effectiveness, the response window for the operator can be very small.
Future generations of UAS will benefit from higher speeds and unprecedented agility since the designers need not worry too much about the ‘g’ effects and push the aircraft to its absolute limit. Greater speed is clearly an advantage in combat. UAS will dominate the OODA (observe-orient-decide-act) loop and operate faster than a defender can observe the threat, orient himself, decide how to respond and act on that decision.
That will apply to all classes of UAS. Highly agile rotary-wing aircraft with tricky trajectories, jet-powered fixed-wing aircraft in combination with stealth technologies, and of course the upcoming threats, hypersonic glide vehicles and hypersonic cruise missiles. Likewise, novel developments such as distributed sensor-to-shooter networks as well as AI-supported or automated decision making will shorten timelines to counter UAS.

Hardening of Drones – No Clay Pigeon Shooting in the Future
For all military vehicles, plating is the usual countermeasure against mechanical threats. For airborne systems, weight aspects are important. Therefore, new plating materials like carbon-reinforced resins were and will be designed which are light and strong. Openings for sensors or engines within the UA’s airframe are weak points for mechanical cracks.
The ongoing miniaturisation for almost all components helps to reduce critical structural elements, to use and distribute multiple components with the same function making the overall system resilient against failure and to integrate most components into the structure shielding them.
Furthermore, military tests have shown that striking drones by conventional projectile weapons is difficult especially if the vehicle is fast and flying at an acute angle to the defence. Also, the UA only will be influenced if relevant components like the navigation system or the engine will be hit. Otherwise, the UA’s mission is impeded.31
As in most military equipment, the hardening against electro-magnetical threats is a standard requirement advancing survivability. High Power Microwave (HPM) threats against UAS and drones can cause three major impacts on the system. Pulse energy can disturb or destroy the sensors as well as important electronics of the drone, huge energy induction can degrade the power system or the structure and architecture effects can hit the combination of the electronic components within the vehicle.
Countering pulse energy specifically designed components with high resistance against Electro-Magnetic Impulses (EMI) were and will be designed. Also, metallic shielding of components or the whole vehicle is an effective countermeasure. Additionally, miniaturization of components will allow designs that can help to reduce a possible energy flow through structural openings. Using shielding, reflectors and heat pipes within the vehicle reduces the electro-magnetic and thermal influence of energy flow. To counter architectural effects, the distribution of relevant components and their distances within the vehicle are important. Using a larger size UA makes it easier to distribute the energy impact, and intelligent design of the system helps to harden it against HPM.32
Avoiding Detection – The Invisible Drone
While most UAS in militaries’ inventories are designed in a ‘traditional’ way, next generations such as the French NEURON or the US Navy’s MQ-25 will incorporate stealth features. The adapted structure of the surface and the inlet reduces the reflections within the radar frequency bands. Specially designed metamaterials can further support this behaviour. Miniaturisation and/or mission-specific varnishing reduce optical visibility. Infra-Red (IR) emissions can be decreased by distributing the occurring thermal energy away from hot spots with heat pipes or radiators.
Low observability flight path planning in the presence of multi-static radar detection systems is a new controls challenge that will increase capabilities for UAS. Current flight path optimization relies on simple aircraft models coupled with detection models with a limited efficiency if confronted with an increasing number of path dependencies and multiple minima requirements. Explorations with variations of the non-linear trajectory generation methods are capable of producing solutions that satisfy observability constraints in the future.33
Likewise, noise detection for surveillance gained more attention in recent years. Passive noise can be reduced by modifying the aircraft structure. Therefore, various vibration-absorbing materials can be used in a limited frequency band. Also, the design of UAS with favourable drag coefficient usually creates less noise during flight than other designs. This can be done, e.g. by modifying the geometry of the wings or the blades. Reduction of low-frequency noise (< 200 Hz) is more challenging than the reduction of higher frequencies. Acoustic metamaterials can support to manipulate the acoustic behaviour in the right way.
Active noise behaviour can be influenced by electromechanical systems which can control the structure, the isolation against sound radiation, or the noise itself. Some of those systems use piezoceramic actuators attached to the skin of the drone or manipulate the engines in a way to actively shape the noise pattern emitted by the drone.34
Quantity Has a Quality All Its Own – Overwhelming the Countermeasures
The threat posed by single UAS and drones has been acknowledged and sophisticated C-UAS technologies have been developed to counter threats from LSS to High Altitude Platforms. The alarming trends for increasingly available, cheap, and operational UAS was showcased in coordinated operations such as the attacks on the Saudi Arabian oil facilities in 2019 or the use of drone swarms at the Winter Olympic Games in 2019.
Swarms of UA and drones in combination with the ability of vehicles to follow a pre-programmed flight-path or to autonomously make decisions based on shared information have the potential to revolutionize the dynamics of conflict in near terms. Swarm size will grow significantly, enhancing the swarm’s behaviour and decisions. A swarm of both large and small drones equipped with different payloads will create a whole that is more capable than the individual parts.35
State-of-the-art C-UAS technology may be able to cope with a bunch of attacking drones, but an offensive swarm is much worse because the drones might be able to adapt to whatever is done to counter them or simply saturate the whole processing chain of countermeasures.
Electronic warfare seems to be the most promising technology to counter swarms since swarm functionality inherently depends on the ability of the drones to communicate and share information. Vulnerabilities to electronic warfare depend on the composition of the drone swarm. Swarms may incorporate drones specifically designed to counter jamming, communication drones serving as relays to share information, or drones equipped with anti-radiation missiles and other anti-jamming weapons.36
Procurement and Costs
‘Governments purchasing defence equipment have a bad record because buying military hardware isn’t like other types of procurement.’ 37
As an example, the United States’ Defense Acquisition Guidebook describes military acquisition as the bureaucratic management and procurement process dealing with a nation’s investments in the technologies, programs, and product support necessary to achieve its national security strategy and support its armed forces including the sustainment of necessary industrial capabilities.38
Similar holistic approaches might vary in granularity across NATO and Partner nations, but in the end, they put required military capabilities in perspective to resources available. Here it is not important what particular acquisition process is used; each has its advantages and disadvantages. Finally, the uncertainties of the future operating environment and the characteristics of defence acquisition will always be challenging, and disappointments are inevitable.39
Market Characteristics
Unlike the commercial markets, the defence procurement process has to operate in a market with limited buyers and limited sellers. That basically results in major tenders occurring on an irregular basis with a variety of well-defined but conflicting objectives pushing the technology envelope. In contrary, the industry has to aggressively bid on military procurements, ‘even if a particular offering doesn’t quite meet the requirements.’40
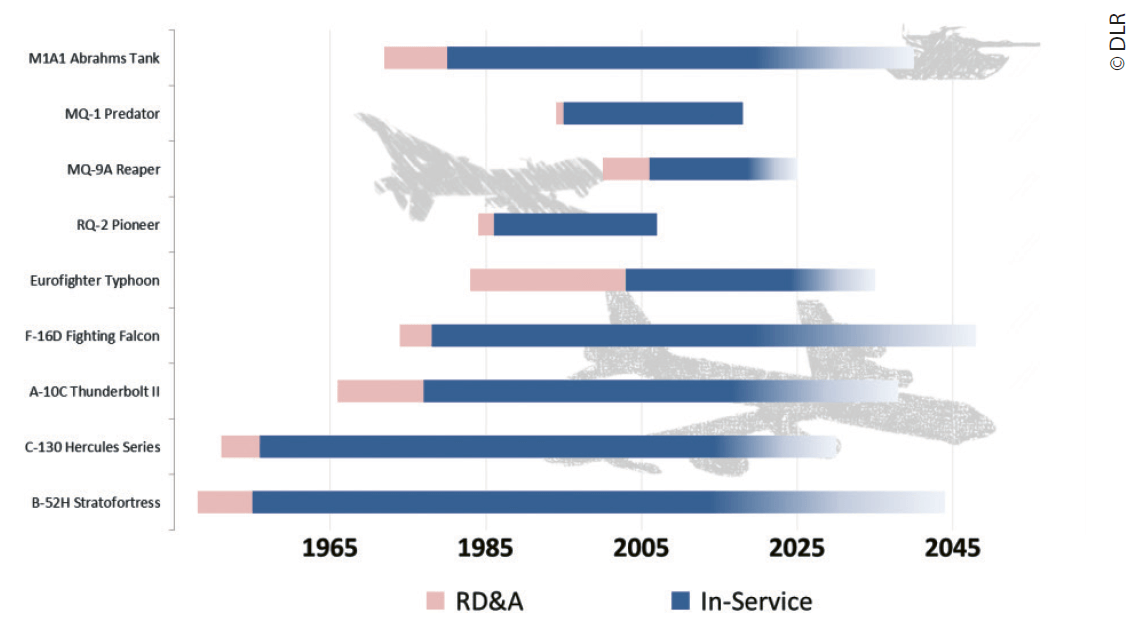
RD&A has to develop equipment requirements based on a very dynamic security environment with limited knowledge of the future. In combination with very long in-service times of 20 or more years, this can often result in fastidious requirements that probably only one or no supplier can meet. In any case, planners are requested to agree on a well-defined set of requirements as a key element of a successful procurement.41
Furthermore, military requirements plus other technical, regulatory and industry policy tend to multiply complexity, risks and costs challenging governmental budgets even further. Even if reasonable, in case secondary objectives overtake the primary ones, project success is jeopardized in most of the cases. The distribution of governmental budgets, yearly planning cycles and appropriation do the rest.
An Example of a National C-UAS Approach – US DoD Procurement
One of the most prominent examples for national C-UAS RD&A can be found in the United States Department of Defence (DoD). ‘In Fiscal Year (FY) 2021 the DoD plans to spend at least USD 404 million on C-UAS research and development and at least USD 83 million on C-UAS procurement’ 42 making it one of the most vital RD&A environments for C-UAS technologies in NATO.
To account for robust defence capabilities, the DoD is developing and procuring several different C-UAS technologies across their four operational services – Air Force, Army, Marine Corps and Navy. This multi-agency approach explicitly includes the assessment and validation of defence capabilities and concepts in real-life exercises looping the feedback in the national RD&A process.
Similar to bigger RD&A projects the DoD has adopted its new ‘Design-Build-Fly’ philosophy to C-UAS technologies accounting for the broad range of challenges outlined in the previous paragraphs. Given the DoD’s strong market position and its user diversity, a wide range of technologies are under consideration. Even if individual products procured by one branch might be obsolete in the near future, complementary technologies from other services would allow for fast adoption and closing capability gaps in relatively short times. In addition, the philosophy does not necessarily include a procurement end-state allowing continuous further development of C-UAS technologies.
Procurement in the EU – National and Future Cooperation?
A fundamentally different problem set can be found in the Euro-pean Union (EU) where the total or relative spending on RD&A are by far lower and nationally scattered compared to the United States. Besides, most European nations do have very specialized services pooling capabilities such as C-UAS in only one branch, resulting in a situation that one service has to provide this specific capability for all services.
When combined, the EU member nations have the second-largest defence budget in the world; a general assessment concluded that the broad diversity significantly hampers military capabilities. Inadequate cooperation amongst the nations results in losses of about EUR 25 to 100 billion each year mainly caused by nationally centric RD&A processes, and, in turn, entailing duplication of work and capabilities. The lack of common defence-related R&D under the umbrella of the EU was worrisome in 2018.43
Furthermore, those scattered national RD&A activities tend to be overloaded with competing requirements and, unlike the services-based US RD&A initiatives, those national procurements cannot be easily adopted by other nations if necessary. Hence, once individual national C-UAS capabilities become obsolete, better-suited solutions from other nations could not be easily operationalized. Also, multi-national RD&A cooperation remains isolated to efforts mainly limited to flagship projects.
Consequently, the EU has implemented the Permanent Structured Cooperation (PESCO) framework complemented by regular capability reviewsiv, capability development prioritiesv and the common European Defence Fund (EDF) slowly developing national RD&A towards multi-national ones. Providing common funding of its research window and co-financing of its capability window the EDF aims towards higher interoperability and strengthening European RD&A in general from 2021 to 2027.44
One of the ongoing PESCO projects aims ‘to develop an advanced and efficient system of systems with C2 dedicated architecture, modular, integrated and interoperable with C2 info-structure, able to counter the threat posed by mini and micro Unmanned Aerial Systems’.45 With only two participating nations this project illustrates the difficulties of common sense and longer-term co-operations. Interestingly, future initiatives such as the European Defence Industrial Development Programme (EDIDP) does not include an individual call dedicated to C-UAS technologies missing the opportunity to collectively focus on this urgent matter.46
Need for Harmonization Between Nations, EU & NATO
While there is a clear need for harmonization of C-UAS capabilities within individual nations, but especially within the two big Alliances, initiatives start to emerge targeting doctrinal and policymaking in this specific area. Stakeholders have recognized that interoperability is more a matter of common requirement sets and standardization rather than a technical challenge. Once that framework is achieved national or multi-national RD&A will be able to provide exchangeable solutions.
While the EU follows a centralized approach capitalizing on its aforementioned toolset as well as common EU funding, in NATO the warfare development of military structures, forces, capabilities and doctrines are led by the Allied Command Transformation (ACT). Compared to the EU, the available budget of NATO ACT or other NATO S&T stakeholders is relatively small and not suited to steer RD&A projects only to support decision making.
NATO relies more on focused initiatives with limited funding and voluntary contributions of its member states to further develop common capabilities. Two prominent examples are the C-UAS Working Group sponsored by the NATO Headquarters that has recently issued its NATO Countering Class I C-UAS Handbook collecting best practices across nations47 and the Low, Slow and Small Threat Effectors study issued by the NATO Industrial Advisor Study Group 200 investigating C-UAS solutions, particularly in the area of soft and hard kill effectors, together with associated Tactics, Techniques & Procedures (TTP).48
Backdrop of C-UAS From a Cost-Benefit Perspective
The outlined dynamic of the C-UAS R&D environment as well as the absence of widely accepted standards results in disadvantageous cost ratios between countermeasures and unmanned air systems. For instance, the unit price per complete FLIR Systems’ Black Hornet Nano can be found between USD 15,000 and USD 20,000,49 while the majority of C-UAS systems cost more than USD 100,000 but covering mainly Class I UAS.50
Currently, UAS are commonly used by militaries as well as non-state actors across the globe and this is expected to grow in the years to come, significantly impacting military operations. Hence, the required area or point defence capabilities need to be deployed in high numbers to cover all necessary altitudes and distances. The combination of relatively high costs and a rather high number of systems will make comprehensive C-UAS capabilities costly as indicated by an initial estimate by the ‘Deutsche Flugsicherung’ for civil airports in Germany.51
So What?
This chapter outlined some basic characteristics of RD&A, which impact the fielding, utilization and effectiveness of C-UAS in general. From the perspective of the authors, there are three major conclusions that can be drawn from it:
The Volatile ‘Silver Bullet’
Even if RD&A would come up with a ‘silver bullet’ to counter Unmanned Air Systems, it might not last long and could become obsolete in several months, setting the C-UAS efforts back to the starting point.
Technological Pace vs Traditional Procurement
If C-UAS solutions are volatile, constant RD&A efforts have to be undertaken to keep up the pace of technology developments leaving traditional procurement processes behind.
No Cost Shortcuts
The necessity of constant efforts has resulted in a relatively high-cost ratio to the disadvantage of C-UAS Systems draining military budgets in peacetime and during conflicts.
Since UAS operations are going to play a major role in conflicts, countering those systems will be a key element for successful operations. From an RD&A perspective those efforts can be supported by a constant information flow between the R&D environment and the C-UAS operator to ensure new findings will be addressed immediately. That includes regular experiments and demonstrations as a natural part of military exercises, mutually bringing together researcher, industry and operator.
Furthermore, the reality of C-UAS might require multiple parallel systems or sub-systems to balance individual capability shortages and to make it harder for UAS to succeed. While for bigger nations that approach seems to be feasible, overall national budget constraints will generally limit the number of C-UAS systems that can be fielded by individual nations. Interoperability amongst individual C-UAS systems and nations embedded in defence frameworks such as NATO and/ or EU will become another key element.
Finally, RD&A cycles for C-UAS need to be shortened to keep pace with the technology development of UAS and drones. In 2019, the current Assistant Secretary of the US Air Force for Acquisition, Technology and Logistics, Dr William Roper, pitched an idea to ‘adopt a rapid approach to developing small batches of fighters with multiple companies, much like the Century Series of aircraft built in the 1950s’.52 Capitalizing on available commercial off-the-shelf systems and sub-systems would allow to field operational C-UAS in shorter periods, probably resulting in a limited capability set of individual systems. By fielding multiple systems and capitalizing on frequent updates, those limits can be overcome and new capability requirements can be addressed immediately.











